Enable Two-Factor Authentication
- Log in to Remote Access Plus
- Navigate to Admin tab -> User Administration -> Secure Authentication
What is two-factor authentication (2FA)?
What is Two-factor Authentication (2FA)? Two-factor authentication (2FA) is a security process that increases the likelihood that a person is who they say they are. The process requests users to provide two different authentication factors before they are able to access an application or system, rather than simply their username and password.
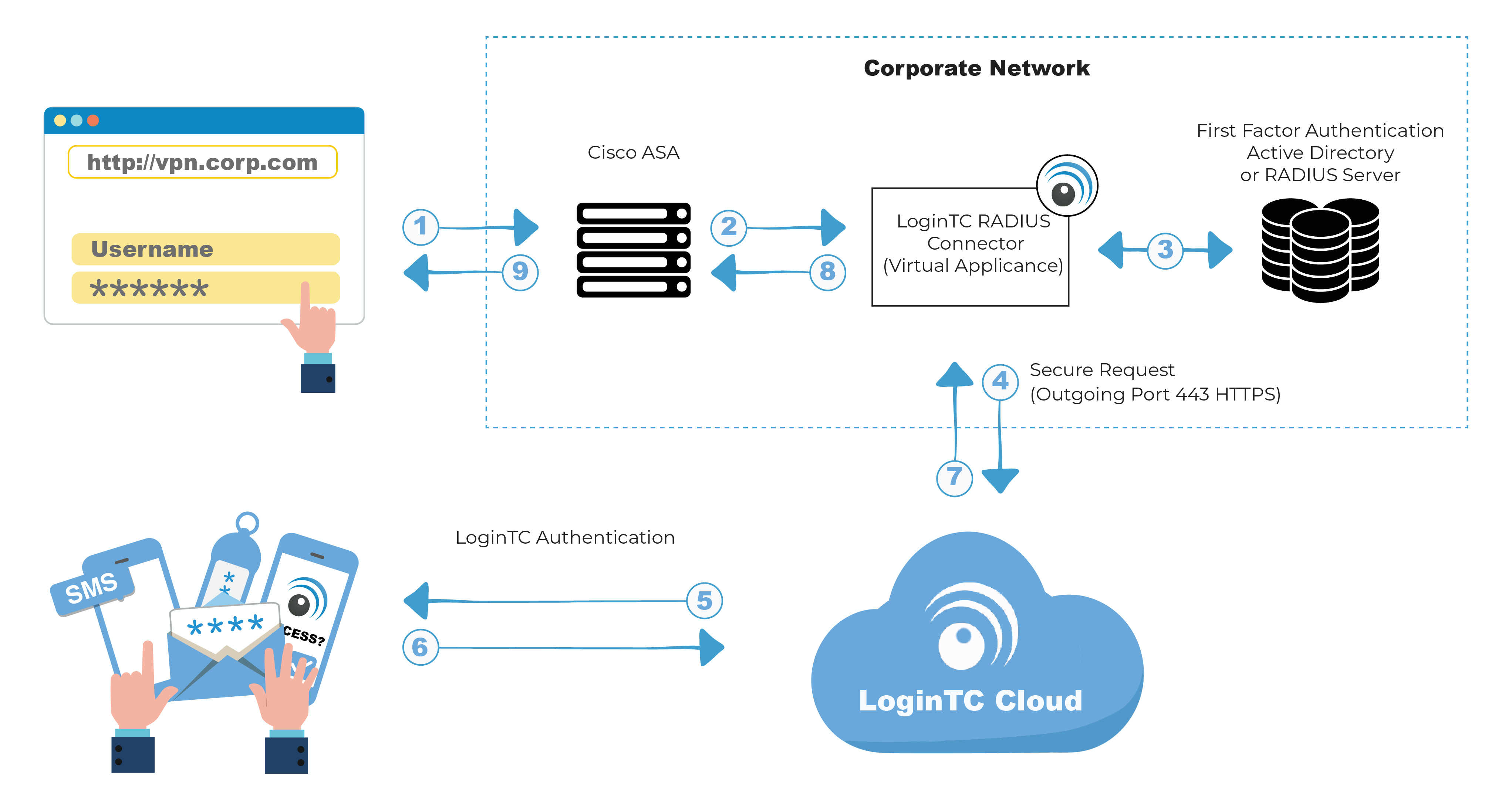
What is secsign ID two-factor authentication for Remote Desktop?
With the SecSign ID Two-Factor Authentication the user can log in to Remote Desktop in just one convenient and quick step – without inconvenient and complex codes. To login the user simply needs to provide user credentials like he is used to, and select the displayed symbol in his mobile app – that’s it. Next level security with minimal complexity.
Which two factor authentication method should I use?
We strongly recommend using Duo Push or U2F as your second factor, because they're most secure and can protect against man-in-the-middle (MITM) attacks, but with Duo's flexibility and customizability, you'll be able to find the adaptive authentication method that meets the unique needs of your diverse user base.
How do I enable 2FA on Remote Desktop?
0:331:53Enable 2FA when opening Remote Desktop Manager - RDM Pro Tip 001YouTubeStart of suggested clipEnd of suggested clipAnd head down to options. And in the options menu there's a security tab.MoreAnd head down to options. And in the options menu there's a security tab.
Can you use MFA with RDP?
On the highest level, multi factor authentication can be added on top of RDP by using: A multi factor authentication vendor/product such as Duo Security, OKTA MFA, … and many more; Using an external Identity Provider (IdP) and the MFA services linked to this IdP.
Is 2 factor authentication the same as MFA?
Multi-Factor Authentication (MFA) is a type of authentication that requires two or more factors of authentication. Two-Factor Authentication (2FA) is a type of authentication that requires exactly two factors of authentication.
What is the best method of two-factor authentication?
Hardware-based 2FA Using a separate piece of hardware like an authenticator device or a U2F security key is the best way to secure any online account.
Can Windows 10 do MFA?
Replace your passwords with strong two-factor authentication (2FA) on Windows 10 devices. Use a credential tied to your device along with a PIN, a fingerprint, or facial recognition to protect your accounts.
How do I secure my remote desktop connection?
Basic Security Tips for Remote DesktopUse strong passwords. ... Use Two-factor authentication. ... Update your software. ... Restrict access using firewalls. ... Enable Network Level Authentication. ... Limit users who can log in using Remote Desktop. ... Set an account lockout policy.
Is 2FA or MFA better?
In general, any 2FA or MFA is more secure than single-factor authentication. However, the security added by any MFA strategy is as strong as the authentication methods chosen by risk professionals.
What's the difference between two step verification and 2FA?
Basically, the difference here is that two factor authentication involves verifying two different factors of authentication before granting access to anyone. On the contrary, two step verification is authentication of one single authentication factor twice, in two steps.
What are the three types of authentication?
The three authentication factors are:Knowledge Factor – something you know, e.g., password.Possession Factor – something you have, e.g., mobile phone.Inherence Factor – something you are, e.g., fingerprint.
What is more secure than 2FA?
First: All other things being equal, MFA is always more secure than 2FA. 2FA is MFA, but not all MFA is 2FA.
What are the different styles of 2 factor authentication?
There are various ways to protect accounts via two-factor authentication: biometrics, one-time passwords, verification codes, QR codes, hardware tokens, and other methods all add another layer of security.
What are some examples of two-factor authentication?
Using two knowledge factors like a password and a PIN is two-step authentication. Using two different factors like a password and a one-time passcode sent to a mobile phone via SMS is two-factor authentication.
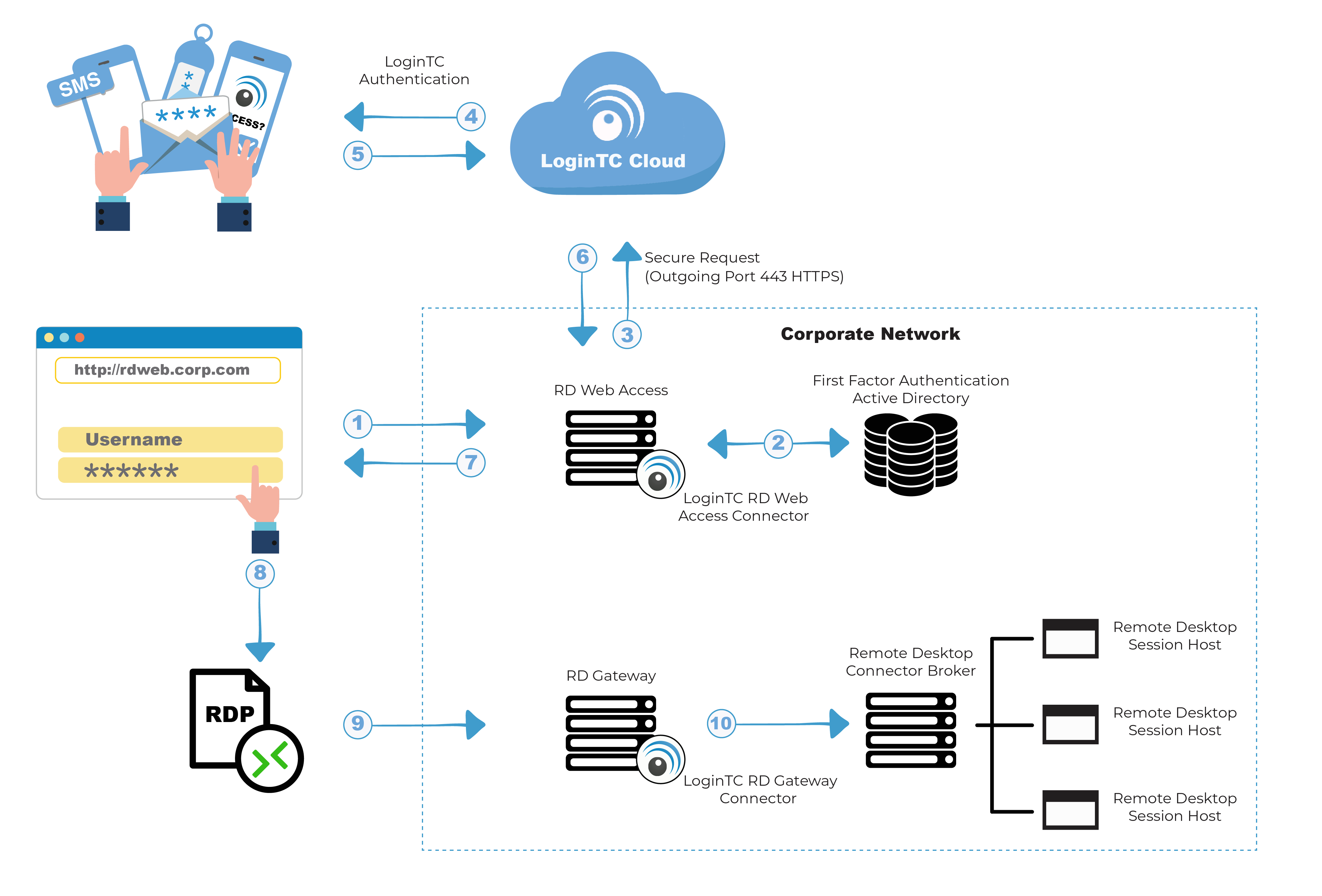
What is Remote Desktop Gateway?
Remote Desktop Gateway (RDG or RD Gateway) is a Windows Server role that provides a secure encrypted connection to the server via RDP. It enhances control by removing all remote user access to your system and replaces it with a point-to-point remote desktop connection.
What is Okta multi factor authentication?
Multifactor Authentication (MFA) is an added layer of security used to verify an end user's identity when they sign in to an application. An Okta admin can configure MFA at the organization or application level.
Is UserLock a decision?
UserLock is a great software that allows us to verify each users' identity, stop password sharing and help avoid security breaches. In a flash, I can control my users' login experience, find/identify users computers and remote in for support.
What is RDP on a computer?
Remote desktop protocol (RDP) is a secure network communications protocol developed by Microsoft. It enables network administrators to remotely diagnose problems that individual users encounter and gives users remote access to their physical work desktop computers.
What is multi factor authentication?
Multi-factor authentication is a security process that enables the use of multiple factors of authentication to confirm a user is who they say they are. MFA means the use of more than one authentication factor to enable a user to access their account.
What is 2FA authentication?
What is Two-factor Authentication or 2FA? Two-factor authentication (2FA) is a security process that increases the likelihood that a person is who they say they are. The process requests users to provide two different authentication factors before they are able to access an application or system, rather than simply their username and password.
What is the difference between 2FA and MFA?
The main difference between 2FA and MFA is that 2FA only requires one additional form of authentication factor. MFA, on the other hand, can include the use of as many authentication factors as the application requires before it is satisfied that the user is who they claim to be.
What is 2FA security?
To answer what is 2FA , a good starting point is remembering that it is a process that moves organizations away from relying on passwords alone to gain entry into applications and websites. 2FA does exactly what it says: provide a two-step authentication process that adds another layer of security to businesses’ defenses.
What is location factor?
A location factor: This is usually guided by the location in which a user attempts to authenticate their identity. Organizations can limit authentication attempts to certain devices in specific locations, depending on how and where employees log in to their systems.
What are the factors used to verify identity?
There are several types of authentication factors that can be used to confirm a person’s identity. The most common include: A knowledge factor: This is information that the user knows, which could include a password, personal identification number (PIN), or passcode. A possession factor: This is something that the user has or owns, ...
How often does a key fob generate a unique code?
They are typically small key-fob devices that generate a unique numerical code every 30 seconds. When a user submits their first authentication request, they can head over to the key fob and issue the code it is displaying.
Two-Factor Authentication (TFA)
Recent security breaches around the world have called for the need to be more cautious about securing customer data in their environment. The majority of these breaches are due to compromised passwords and unused account privileges.
Enable Two-Factor Authentication
When you enable Two-Factor Authentication, all the users will be required to provide an additional security code to login and access Remote Access Plus. To enable TFA,
Using an Authenticator App
The authenticator app can be Zoho OneAuth, Google Authenticator, MS Auth, DUO Auth, etc.
Using Email
When you choose email as a mode for two-factor authentication, the OTP will be generated by Remote Access Plus and sent to the user's registered email address. User will have to use the OTP received in the email in addition to the regular password. User should have access to email, in order to access Remote Access Plus server.
What is 2FA authentication?
What is 2FA? Two-factor authentication (2FA) is a specific type of multi-factor authentication (MFA) that strengthens access security by requiring two methods (also referred to as authentication factors) to verify your identity.
What is location factor authentication?
If a user had registered an account in one country, for example, and suddenly there are login attempts from another, location factors could trigger and attempt to verify the identity of the new user. Many location factors are based on the IP address of the original user and compares the address to that of the new attempt to access information.
Why is 2FA important?
2FA is an effective way to protect against many security threats that target user passwords and accounts , such as phishing, brute-force attacks, credential exploitation and more.
Why do social media companies use 2FA?
Social media platforms and agencies use 2FA to protect the personal data of billions of users worldwide. To protect these users, social media companies like Facebook use Duo’s push-based authentication to shield their developers from hacking attempts when working on the company’s internal networks.
What is the most obvious inherence factor used today?
Inherence factors of authentication verify the identity of a user by using attributes that would belong only to that user. Fingerprint scanning is the most obvious inherence factor used today. Fingerprints are unique to individuals, so many organizations use them as a way to confirm who their users are.
How does time factor authentication work?
Time factors of authentication verify the identity of a user by challenging the time of the access attempt. This is based on the assumption that certain behaviors (like logging into a work computer) should happen within predictable time ranges. If an attempt to access a platform happens outside of the usual time range, the attempt can be challenged or terminated until a user can verify their identity.
What is the knowledge factor?
Knowledge Factor. The knowledge factor verifies identity by requesting information only an individual user would know. The most common example of a knowledge factor of authentication is a password. A user’s password should be private only to them, allowing them to use it as a method to confirm their identity.
What is an example of authentication?
In the scope of cybersecurity, the most common example of authentication is logging into a service on the web, such as signing into Gmail in a web browser or logging in on the Facebook app. When a user provides a username and password combination, the service can confirm these details and use them to authenticate the user.
Why is 2FA important?
For this reason, 2FA is becoming more and more commonplace. Stronger identity verification has also increased in importance as remote workforces become more common. Many company employees no longer come into the office and instead work remotely.