Types of Remote Access: Benefits & Disadvantages
- VPNs: Virtual Private Networks. When employees need to remotely access their company files, a virtual private network (VPN) is often the tool of choice.
- Desktop sharing. Desktop sharing is another way organizations can provide remote access to users. ...
- PAM: Privileged Access Management. To go beyond VPNs and desktop sharing, you need an alternative that can manage identities closer than mere IAM technologies such as Active Directory.
- VPAM: Vendor Privileged Access Management. Many organizations need to provide privileged accounts to two types of users: internal users (employees) and external users (technology vendors and contractors).
What are the different types of remote access?
- Secure Authentication The remote user must be authenticated according to your company. ...
- Secure Connection Is the connection securely encrypted so no other person can get access to your information?
- Access level Can the remote party access more resources than needed? ...
What is most common for remote access?
The top RATs
- The hacker’s choice: FlawedAmmyy. When trying to identify which malware variant is the most effective, it’s useful to take a look at what hackers are actively using.
- Free and open-source: Quasar. For those who what a free and open-source RAT (to avoid potential backdoors), Quasar RAT is widely recommended.
- Mobile access (iOS): PhoneSpector. ...
What programs allow remote access?
The best remote desktop software right now
- RemotePC. RemotePC is a hugely-popular remote computer access application that’s suitable for both home and—in particular—for business users.
- Zoho Assist. Cloud-based Zoho Assist is one of our favorite remote access tools because it enables you to access almost any device.
- Splashtop. ...
- Parallels Access. ...
- LogMeIn Pro. ...
- Connectwise Control. ...
- TeamViewer. ...
What are the best practices for remote access?
To scan roles by using the BPA GUI
- Do one of the following to open Server Manager if it is not already open. ...
- In the navigation pane, open a role or group page. ...
- On the Tasks menu of the Best Practices Analyzer tile, click start BPA Scan.
- Depending on the number of rules that are evaluated for the role or group you selected, the BPA scan can require a few minutes to finish.
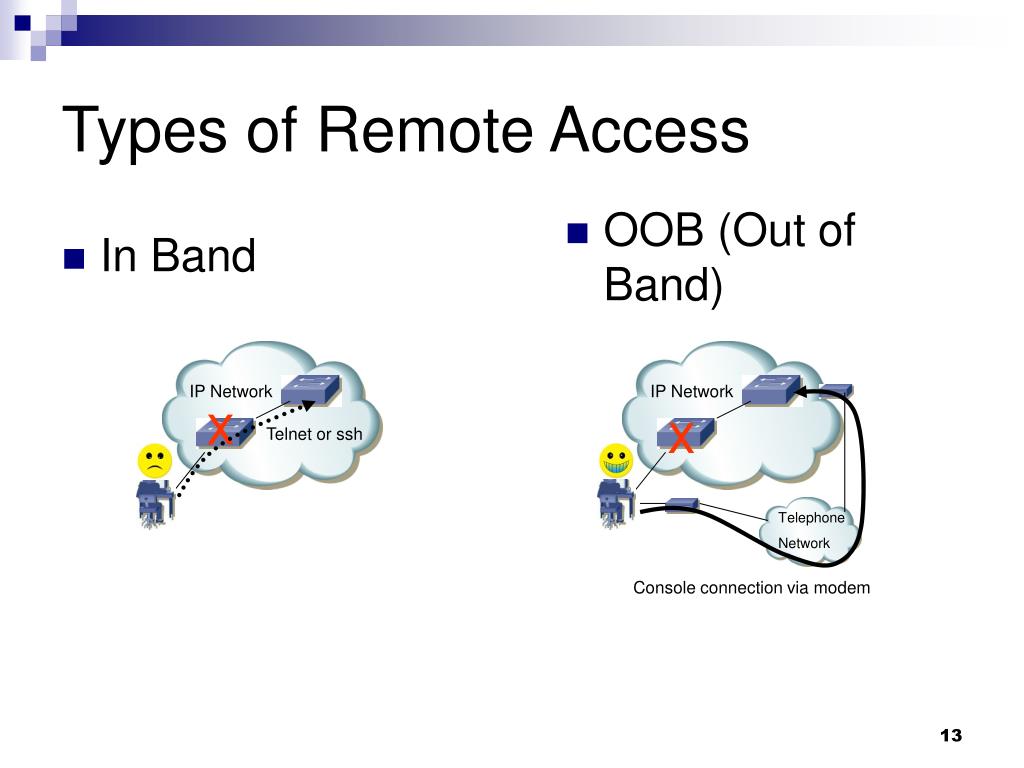
What are the different types of remote access methods?
Remote Access Control MethodsDirect (Physical) Line. The first direct remote access control that can be implemented is a direct line from a computer to the company's LAN. ... Virtual Private Network. Another method which is more common is establishing a VPN. ... Deploying Microsoft RDS.
What is remote access examples?
Accessing, writing to and reading from, files that are not local to a computer can be considered remote access. For example, storing and access files in the cloud grants remote access to a network that stores those files. Examples of include services such as Dropbox, Microsoft One Drive, and Google Drive.
What is considered remote access?
Remote access is the ability for an authorized person to access a computer or network from a geographical distance through a network connection. Remote access enables users to connect to the systems they need when they are physically far away.
What are the uses of remote access?
Remote access, also known as remote login, is the ability to access the data stored on a computer from a remote location. It enables you to open, edit, and save files located on your device from anywhere in the world. This ability is handy for offsite workers, travelers, and those who work out of office.
What is remote access VPN?
A remote access virtual private network (VPN) enables users who are working remotely to securely access and use applications and data that reside in the corporate data center and headquarters, encrypting all traffic the users send and receive.
What is remote access on router?
Remote-access-router definition Filters. A network device used to connect remote sites via private lines or public carriers. The router is required at both ends and provides the protocol conversion between the internal network (LAN) and the external network (WAN). See remote access concentrator and remote access server ...
How do I set up remote access to my computer?
Set up remote access to your computerOn your computer, open Chrome.In the address bar, enter remotedesktop.google.com/access .Under “Set up Remote Access,” click Download .Follow the onscreen directions to download and install Chrome Remote Desktop.
What does remotely mean in business?
Remote work is the practice of employees doing their jobs from a location other than a central office operated by the employer. Such locations could include an employee's home, a co-working or other shared space, a private office, or any other place outside of the traditional corporate office building or campus.
What are the two types of users that need privileged accounts?
Many organizations need to provide privileged accounts to two types of users: internal users (employees) and external users (technology vendors and contractors). However, organizations that use vendors or contractors must protect themselves against potential threats from these sources.
What are some applications that can be shared on desktop?
There are many applications made possible by desktop sharing including remote support, webinars, and online conferences with audio and visual content (presentation sharing), and real-time global collaboration on projects.
Can anyone log into a desktop sharing tool?
Anyone, anywhere, can log into a desktop sharing tool if they have the credentials, meaning they have access to the whole network as if they are in the building. During a remote support session, if an employee surrenders control of their machine to a remote rep whose account has been compromised, your company’s internal sensitive files could become visible to bad actors and used for nefarious purposes.
Is VPN good for remote access?
VPNs may be good for internal employees, but are not optimal for third-party vendors. Desktop sharing tools may be useful for desktop support and helpdesk, but are not good for complex enterprise remote support. PAM provides improvements over VPN and desktop sharing, but there is only one solution that combines the best of all these types of remote access technologies into one and is purpose-built for vendors and doesn’t include any of the drawbacks: VPAM.
Long-term Remote Access Could Be the Norm for Some Time
Some knowledge workers are trickling back to their actual offices, but many more are still at home and will be for some time. Global Workplace Analytics estimates that 25-30% of the workforce will still be working from home multiple days a week by the end of 2021.
SASE Provides a Simpler, More Secure, Easily Scalable Solution
Cato’s Secure Access Service Edge (or SASE) platform provides a great alternative to VPN for remote access by many simultaneous workers. The platform offers scalable access, optimized connectivity, and integrated threat prevention that are needed to support continuous large-scale remote access.
SASE Supports WFH in the Short-term and Long-term
While some workers are venturing back to their offices, many more are still working from home—and may work from home permanently. The Cato SASE platform is the ideal way to give them access to their usual network environment without forcing them to go through insecure and inconvenient VPNs.
Choosing a Virtual Desktop Solution
Here’s a guide to things you should look for when selecting a VDI or remote access platform for your organization:
Mendy Newman
Internet Surfing Separation: Effective Security or Draconian Constraint?
What are the types of remote access?
Traditionally, enterprises used modems and dial-up technologies to allow employees to connect to office networks via telephone networks connected to remote access servers. Devices connected to dial-up networks use analog modems to call assigned telephone numbers to make connections and send or receive messages.
How does remote access work?
Remote access is accomplished with a combination of software, hardware and network connectivity.
What are the Types of Remote Access?
In the past, remote access was possible by hardwiring to a telephone network. Analog modems and dial-up technology allowed two different devices to interact with one another by calling assigned phone numbers.rThis has changed significantly with broadband technology.Today, remote access is possible via:
What is remote access software?
Remote access software enables users to connect to computers, servers, or networks remotely. There are a few ways to use it:
What is VPN for branch offices?
VPN itself was specifically developed for remote employee access and interconnectivity between branch offices. It provides a way to securely and remotely access resources on company servers with verified login credentials. Remote access works by utilizing software, hardware, and network configurations. .
Why do we need remote access protocol?
It also helps keep your server secure and protected against hacks and leaks. There are several protocols for doing this:
How does remote access work?
Remote access works by utilizing software, hardware, and network configurations. . Despite the recent uptick in trend, this isn’t a new concept. In fact, it was even possible to access remote files before the advent of the internet.
Why is it important to shift to remote work?
The shift towards remote work benefits both employee and employer. Businesses don’t have to pay for office space or the associated overhead costs. This allows them to save money and focus on the future success of their business. Employees also save money on commuting and can live in more affordable areas outside of the city.
Why is remote access important?
Remote access also ensures that a company can hire whoever they want without the need for relocation. They can work with the best in the industry, no matter where they live, cutting out geographical restraints for both employees and employers. Another benefit is the easy availability of technical support.
What is remote access protocol?
A remote access protocol is responsible for managing the connection between a remote access server and a remote computer. It’s necessary for desktop sharing and remote access for help desk activities. The primary remote access protocols in use today are the Serial Line Internet Protocol (SLIP), Point-to-Point Protocol (PPP), ...
What is managed services provider?
As a managed services provider (MSP), you likely already work with remote access protocols on a daily basis. But learning how to best explain the various types of remote access protocols and their advantages and disadvantages to customers is critical in helping them understand your decisions—and why they should trust you and your services.
Can you use a RAS modem on a Windows server?
With a RAS setup, you can connect a modem to a Windows 2000 or Windows NT server and configure the modem as dial-out only, dial-up only, or a combination of the two. RAS can only provide LAN access to remote users. It doesn’t let LAN users use the modem to, for example, dial their AOL account.
Is RDP the same as ICA?
RDP offers the same core functions as ICA, although there are some limitations. RDP provides remote access for Windows clients only, while ICA can provide access for numerous platforms. ICA also offers support for automatic client updates, publishing an app to a web browser, and more.
What is the easiest program to use for remote access?
AeroAdmin is probably the easiest program to use for free remote access. There are hardly any settings, and everything is quick and to the point, which is perfect for spontaneous support.
How to access remote computer?
There are a couple of ways to access the remote computer. If you logged in to your account in the host program, then you have permanent access which means you can visit the link below to log in to the same account in a web browser to access the other computer.
How to enable remote desktop access to a computer?
To enable connections to a computer with Windows Remote Desktop, you must open the System Properties settings (accessible via Settings (W11) or Control Panel) and allow remote connections via a particular Windows user.
How does remote utility work?
It works by pairing two remote computers together with an Internet ID. Control a total of 10 computers with Remote Utilities.
What is the other program in a host?
The other program, called Viewer, is installed for the client to connect to the host. Once the host computer has produced an ID, the client should enter it from the Connect by ID option in the Connection menu to establish a remote connection to the other computer.
What is the name of the program that allows you to access a Windows computer without installing anything?
Install a portion of Remote Utilities called Host on a Windows computer to gain permanent access to it. Or o just run Agent, which provides spontaneous support without installing anything—it can even be launched from a flash drive.
Can you run DWAgent on your own computer?
The host has two options: download the DWAgent, and then run it for on-demand, one-time access (great for tech support), or install it for permanent remote access (ideal if it's your own computer).
What are remote hackers?
With the rise of a remote working population, “remote hackers” have been re-emerging as well. These remote hackers take advantage of remote working technologies like video conferencing tools, enterprise VPNs, and other remote access solutions that have become popular during the COVID-19 crisis.
How do remote hackers reach unsuspecting victims?
Remote hackers use various malware deployment methods; the most common (and probably the easiest) way for hackers to reach unsuspecting victims is through phishing campaigns.
