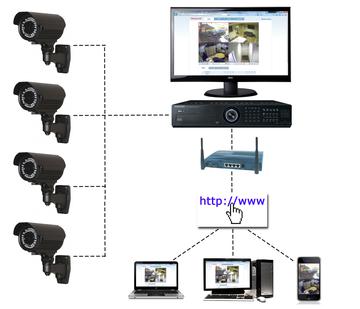
Understanding the Elements of a Remote Access Policy
- Remote Access Conditions. Remote access conditions consist of one or more attributes that can be compared against a connection attempt by a remote user.
- Tunnel Type Windows Groups. The name of the RADIUS client that is requesting authentication. ...
- The IP address of the client. ...
- Remote Access Permissions. ...
- A Exam Warning. ...
- Remote Access Profiles. ...
- Test Day Tip. ...
What is remote access and how can I use it?
Windows 10 Fall Creator Update (1709) or later
- On the device you want to connect to, select Start and then click the Settings icon on the left.
- Select the System group followed by the Remote Desktop item.
- Use the slider to enable Remote Desktop.
- It is also recommended to keep the PC awake and discoverable to facilitate connections. ...
What does remote access mean for my company?
Remote access can mean different things to different companies. It could mean accessing a client database hosted on a server outside of your company’s network. It could mean accessing an application that’s critical to your business from anywhere at any time via a web browser. It could also mean having the ability to do your entire day’s ...
What is an example of remote access?
- Remote Access Plus is an enterprise remote desktop access solution that can access devices running on Windows, Mac, and Linux.
- This tool enables users to remotely control any device irrespective of time and location.
- Users can zero in on the root cause of the problems effortlessly using Event Viewer, System Manager, File Manager, and much more.
What is most common for remote access?
Video conferencing software allowed remote teams to stay connected during the pandemic ... is the world’s first laptop with a collaboration touchpad that provides quick access to microphone mute/unmute, video on/off, screen share and chat in Zoom meetings.

How do I use remote access?
Set up remote access to your computerOn your computer, open Chrome.In the address bar, enter remotedesktop.google.com/access .Under “Set up Remote Access,” click Download .Follow the onscreen directions to download and install Chrome Remote Desktop.
What happens if you give someone remote access to your computer?
This can be even worse than just conning you out of money, as undetected malware can allow hackers to steal your identity, including your passwords and financial information, over and over again, even if you get new passwords and account numbers.
What is remote access examples?
Accessing, writing to and reading from, files that are not local to a computer can be considered remote access. For example, storing and access files in the cloud grants remote access to a network that stores those files. Examples of include services such as Dropbox, Microsoft One Drive, and Google Drive.
What is needed for remote access?
Remote computer access requires a reliable internet connection. You'll need to activate or install software on the device you want to access, as well as on the device — or devices — you want to use to get that access.
Can someone access my computer remotely without me knowing?
"Can someone access my computer remotely without me knowing?" The answer is "Yes!". This could happen when you are connected to the internet on your device.
How do you know if your PC is being monitored?
How to Check If Your Computer Is Being MonitoredLook for Suspicious Processes. Suspicious processes may indicate that your computer is being monitored. ... Run Antivirus Software. Antivirus software can reveal whether or not your computer is being monitored. ... Evaluate Ports. Another tip is to evaluate your network's ports.
What are the three main types of remote connections?
Remote Access Control MethodsDirect (Physical) Line. The first direct remote access control that can be implemented is a direct line from a computer to the company's LAN. ... Virtual Private Network. Another method which is more common is establishing a VPN. ... Deploying Microsoft RDS.
How do I connect remotely to another computer?
First, you or someone else must physically sign into the PC you want to remotely access. Enable Remote Desktop on this computer by opening Settings > System > Remote Desktop. Turn on the switch next to Enable Remote Desktop or Remote Desktop. Click Confirm to enable the setting.
What is remote access and how does IT work?
Remote access is the ability for an authorized person to access a computer or network from a geographical distance through a network connection. Remote access enables users to connect to the systems they need when they are physically far away.
What are the types of remote access?
The primary remote access protocols in use today are the Serial Line Internet Protocol (SLIP), Point-to-Point Protocol (PPP), Point-to-Point Protocol over Ethernet (PPPoE), Point-to-Point Tunneling Protocol (PPTP), Remote Access Services (RAS), and Remote Desktop Protocol (RDP).
What would be some of the risks in allowing remote access?
Many remote access security risks abound, but below is a list of the ones that jump out.Lack of information. ... Password sharing. ... Software. ... Personal devices. ... Patching. ... Vulnerable backups. ... Device hygiene. ... Phishing attacks.
Can you get a virus from remote access?
Many remote access software solutions don't scan the remote computer for viruses or malware. If your home or work PC has been infected, and you're using it to access your office network remotely, then a hacker could easily install malware onto your business's servers and spread to every machine in your office.
What is remote access?
Remote access is the act of connecting to IT services, applications or data from a location other than headquarters or a location closest to the data center. This connection allows users to access a network or computer remotely via an internet connection or telecommunications. Secure remote access benefits include: ...
What are the benefits of remote access?
Remote access can bring many benefits to a business, from lowering costs to increasing worker satisfaction and productivity.
Why is Citrix remote access important?
Remote access is great for teleworkers, contractors, those who work from home , or individuals displaced from their home office due to natural disaster or other circumstances. It is valuable for businesses to have a strategy for allowing remote access to their users. Employees may have the flexibility to work from home, or have a plan in place if they are not able to go into the office during a natural disaster. View Citrix Remote PC Access
What happens when an employee is displaced due to a business continuity disruption?
If an employee has been displaced due to a business continuity disruption, they can continue to be productive using a secure remote access connection.
How does remote access benefit a business?
Remote access can bring many benefits to your business, from lowering costs to increasing worker satisfaction and productivity.
Why do we need single sign on?
In order to ensure a high-quality user experience while still maintaining security and control , IT teams must provide users with single sign-on (SSO) across all applications. By leveraging contextual access controls and multi-factor authentication, IT can maintain end-to-end oversight across all application traffic while users can connect from anywhere.
What is Citrix Networking?
With Citrix Networking and SmartAccess, organizations have the capability to control printers, client devices, session connectivity, and reactive security postures. Admins are also able to leverage the full capabilities of Citrix Analytics to collect data for improving app performance, supporting continuous operations, and enhancing security.
What is a RAS server?
Depending on the size of your network, the RAS server can be your primary network server or an additional server on the network that is specifically charged with handling remote access connections. Configuring a server for remote access involves the following tasks :
Can a computer connect to a network using a modem?
Although wireless technology will definitely change our options for connecting to a network from a remote location in the next few years , the asynchronous modem still serves as the typical connection device and uses the public phone lines as the communication conduit . Any desktop PC or laptop computer can be outfitted with a modem. Almost all client operating systems also provide a dial-up client that can be used to connect to a network using a modem. Millions of people use modems and dial-up clients to connect to their Internet service providers so that they can check their email and browse the World Wide Web.