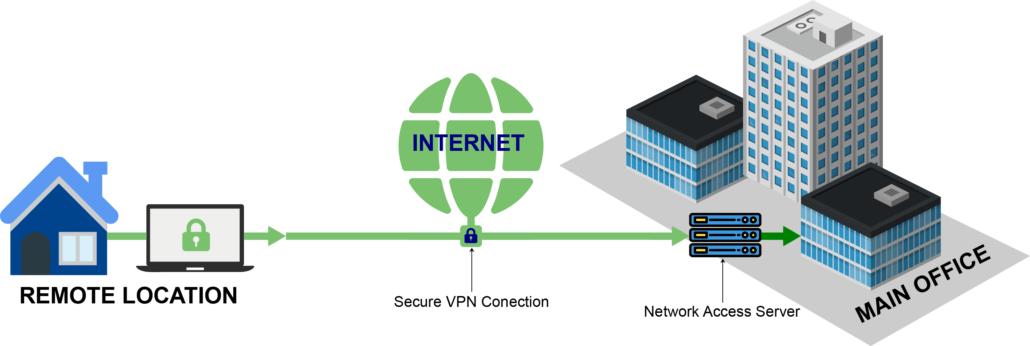
How do I access my VA remote?
You may request remote access by visiting the Remote Access Self Service Portal ( only available while on VA's internal network). Please note the Self-Service Portal is only accessible from within the VA network, it is not externally accessible.
Is Va Citrix down?
Va.gov is UP and reachable by us.
Can I log into my VA email from home?
You can sign in to VA.gov with any of these 4 accounts: Login.gov. ID.me. My HealtheVet. DS Logon.
How do I use my VA PIV card?
If you have a PIV card, insert your PIV card into the reader. If you do not, choose the username and password option, enter your username and password. For browsers other than Internet Explorer an *. ica file will download once you select an option and will show in the bottom-left of your browser.
Why can't I access my HealtheVet?
If you are unable to view your medical data on My HealtheVet, please contact your local VA medical center Release of Information office to obtain copies, to which you are entitled. Please call ahead to confirm any upcoming VA appointments. Your local VA pharmacy can answer questions about your prescription refills.
Why can't I log into the VA website?
First, try resetting the password for the account you use to sign in to VA.gov: Reset your password on the My HealtheVet website. Reset your password on the DS Logon website. Reset your password on the Login.gov website.
Does the VA have an online portal?
WASHINGTON — The U.S. Department of Veterans Affairs (VA) announced Dec. 18, that Veterans now have digital access to patient statements through AccessVA using their secure information for DS Logon, ID.me or MyHealtheVet Premium.
What sites use DS Logon?
Premium DS Logon is a secure identity credential that Veterans and service members can use to sign in to several websites, like VA.gov, My HealtheVet, and eBenefits, with one username and password. This is called single sign-on.
How do I use Citrix Gateway?
Install the Citrix Secure Access agent for WindowsIn a web browser, type the web address of Citrix Gateway.Type the user name and password and then click Logon.Select Network Access and then click Download.Follow the instructions to install the plug-in.
Who gets a PIV card?
A PIV Card Applicant is anyone who is eligible to apply for a VA PIV Card. To be eligible, you must: Be an employee, contractor, affiliate or volunteer who will work with VA for more than six months continuously or more than 180 aggregate days in a given year, and.
What is VA PIV card?
The PIV Card The Personal Identity Verification (PIV) card is an identification card issued by a federal agency that contains a computer chip, which allows it to receive, store, recall, and send information in a secure method.
What is a PIV exemption?
Personal Identification Verification (PIV) Exemptions Process. Scenarios for Temporary Exemption: New User without PIV Issuance. 1. If a new user has been issued a VA network account, but not a PIV credential, the user may contact Enterprise Service Desk (ESD) at (855) 673-4357 to request a temporary exemption.
Is there an issue with Citrix today?
Citrix.com is UP and reachable by us.
Why is my Citrix workspace not working?
The most common cause why Citrix Workspace (formerly Citrix Receiver) is not working is actually the Internet connection you're using. When you have a slow, or unreliable Internet connection, Citrix Workspace isn't able to work properly.
What's wrong with Citrix?
The main problem with Citrix is its overly complex architecture and licensing structure. A typical Citrix infrastructure has too many components and interdependencies.
Has Citrix been hacked?
Hackers breached the agency's Citrix servers Tracked as CVE-2019-19781, this vulnerability allows attackers to bypass authentication on Citrix ADC devices and execute malicious code.
Remote Access
A remote access account with either Athens or LibLynx allows you to access library resources with a single username and password while at home or on travel without VPN. We are transitioning from Athens to LibLynx, so Athens will eventually go away.
LibLynx
Here is a list of libraries that have LibLynx now. If your facility is on this list go to the LibLynx page for information and instructions.
How to request remote access to VA?
Go to the VA home page (open Internet Explorer on a VA computer-this should be the home screen) Look at the links under the “Top Facility Resources” column on the webpage and click on “Remote Access Request” From there, click on “Self Service Portal” at the top of the page to “Request Access” for Remote Access.
What is the best URL for VHA21?
Requires one of two options: 1.Use of PIV card instead of your vha21vhasfcxxxxxxdomain name and password, or; 2.Use of a “One Time Password” (a six-digit number generated by the MobilePASSApp) in addition to your vha21vhasfcxxxxxx credentials 3.Best URL is citrixaccess.va.gov; other options are vacagwest.vpn.va.gov, vacageast.vpn.va.gov, vacagnorth.vpn.va.gov, vacagsouth.vpn.va.gov 4.Your Mac/PC/tablet must have Citrix Receiver installed (www.citrix.com) For Mac, Safari is the best browser
What is the VA security domain?
The Security Domain describes what VA must do to protect sensitive personal customer and employee information and ensure its cyberspace ecosystem is secure, ready, resistant, and resilient from threats, unauthorized access, and vulnerabilities. According to the Conceptual Metamodel below, the scope of this Domain includes security-related strategies, plans, laws, policies, regulations, capabilities, standards, practices, and performance measures.
What is user identity authentication?
User Identity Authentication – This Enterprise Design Pattern describes the “To-Be” state for VA internal (Personal Identity Verification [PIV]-enabled VA employees, contractors, and volunteers), as well as external user identity authentication ( business partners, Veterans, and others who access VA resources from outside VA’s networks).
Will the VA EA be updated?
As the Enterprise Cybersecurity Strategy continues to mature and evolve, the VA EA will be updated. This will include the addition and integration of all relevant security requirements to support critical aspects of the strategy that must be followed and enforced within VA business processes during the development, implementation, and execution of IT solutions.
Using Your PIV Card
Before you get started, make sure your Windows machine has all patches and hotfixes applied.
Things to be aware of
Chrome and Edge may attempt to open the last site you went to based on the browser settings. To prevent this issue, please change this setting to open a New Tab page (preferred) or a specific page when you open a new browser window.

VA EA Security Domain
Domain Scope
- The Security Domain describes what VA must do to protect sensitive personal customer and employee information and ensure its cyberspace ecosystem is secure, ready, resistant, and resilient from threats, unauthorized access, and vulnerabilities. According to the Conceptual Metamodel below, the scope of this Domain includes security-related strategie...
Relationships
- The Security Domain information is closely linked to all other domains because security is integral to the overall security posture and health of an organization and/or system. These linkages: 1. Describe the relationships between the Department’s cybersecurity strategy, goals, and objectives and enabling capabilities, functions, business processes, information, infrastructure, and technol…
Future Enhancements
- As the Enterprise Cybersecurity Strategy continues to mature and evolve, the VA EA will be updated. This will include the addition and integration of all relevant security requirements to support critical aspects of the strategy that must be followed and enforced within VA business processes during the development, implementation, and execution of IT solutions.
Key EA Artifacts Currently Available
- Strategic Guidance 1. Enterprise Cybersecurity Strategy and Enterprise Cybersecurity Strategy Fact Sheet– focuses on building a comprehensive cybersecurity capability that spans VA and the cyberspace ecosystem in which VA personnel, its customers, and its partners operate. White Papers/Tech Insights 1. List of security related Tech Insights: Models, Patterns, and Reports 1. E…