- Identify users.
- Audit all high-risk access points.
- Implement and enforce vendor remote access policies.
- Apply access controls.
- Monitor user access.
- Automate vendor remote access.
Is remote vendor access the path of least resistance?
A vendor is frequently seen as the path of least resistance for a bad actor to get into a network or multiple networks. Let’s look at the best practices associated with third-party remote vendor access.
Why do vendors use remote access tool licenses?
Since vendors don’t need constant access to your network, they often use one remote access tool license and share generic logins and passwords across technicians. This makes the credentials easy for hackers to guess. What’s more, the vendor’s ex-employees often retain remote access to your systems.
Why is it important to manage third-party remote vendor access?
Because of this, it’s imperative that businesses have much more control over and manage their third-party remote vendor access. Beyond that, in order to limit liability, enterprises need a detailed log of exactly what individuals did while they were connected to their network. If you don’t have that, you’re not secure, accountable, or compliant.
Should vendors use VPNs for remote network access?
While VPNs are ideal for employee remote network access, for a vendor, this type of access can be both limiting and frustrating. When using VPNs to access customer networks, vendors may get dropped off their own network and not be able to access their local knowledge-base or hard drive.

What should be included in a remote access policy?
What Should You Address in a Remote Access Policy?Standardized hardware and software, including firewalls and antivirus/antimalware programs.Data and network encryption standards.Information security and confidentiality.Email usage.Physical and virtual device security.Network connectivity, e.g., VPN access.More items...•
What are the examples of remote user security policy best practices?
Best Practices For Remote Access SecurityEnable encryption. ... Install antivirus and anti-malware. ... Ensure all operating systems and applications are up to date. ... Enforce a strong password policy. ... Use Mobile Device Management (MDM) ... Use Virtual Private Network (VPN) ... Use two-factor authentication.More items...•
What are the most important criteria for selecting remote access devices?
Deployment, ease of use, mobile access, security, and scalability are key features businesses need to look for when considering a remote access solution.
What are the five elements of a remote access security readiness review?
The review examined cybersecurity at the governance layer and identified five critical pillars key to cybersecurity readiness: culture, people, structure, processes, and resources.
How do I ensure secure remote access?
How to Ensure Secure Remote Access for Work-from-Home EmployeesIssue Secure Equipment to Remote Employees.Implement a Secure Connection for Remote Network Access.Supply a VPN for Secure Remote Access.Empower Remote Employees through Education and Technology.
How do I make remote access reliable and safe?
Basic Security Tips for Remote DesktopUse strong passwords. ... Use Two-factor authentication. ... Update your software. ... Restrict access using firewalls. ... Enable Network Level Authentication. ... Limit users who can log in using Remote Desktop. ... Set an account lockout policy.
What should a company consider when looking at adding remote employees?
These expectations should include work hours, availability, deadlines, meeting scheduling and attendance, work submission and more. When setting these requirements consider the differences between remote and in-house workers.
What is a preferred security measure for remote access?
Virtual Private Networking (VPN) is often considered the best approach in securing trans-network communication.
What is an example of remote control operations for providing security to an organization?
Popular examples include Remote Desktop Protocol (RDP) and Virtual Network Computing (VNC). While remote desktop access can have convenience advantages, this method is not typically recommended as it introduces significant security risks to the corporate network.
What's your best practice in ensuring that you are following the standard security protocols?
Top 10 Security Practices& 2. ... Use a strong password. ... Log off public computers. ... Back up important information ... and verify that you can restore it. ... Keep personal information safe. ... Limit social network information. ... Download files legally. ... Ctrl-ALt-Delete before you leave your seat!More items...
Which policy defines the security controls while working remotely?
ISO 27001 controls for remote working: A 6.2. 1 – Mobile device policy.
What are some effective ways to get user buy in of security policies?
3 Tips for Driving User Buy-in to Security PoliciesTip 1: Relax Security Rules. As a security professional, I understand the value of advocating for the strongest security possible. ... Tip 2: Engage Users with Meaningful Training. ... Tip 3: Explain Why. ... Related Content:
Why is remote access important?
It is essential for these individuals to have safe, anytime, anywhere access to corporate networks and services.
What happens if you give access to an outsider?
Recognize that granting system access to an outsider lowers your security level to that of the external provider. If they lack strong security controls, they become your weakest link. If a hacker compromises their system, that partner can become a backdoor into your environment .
What percentage of Verizon network intrusions exploited weak or stolen credentials?
According to Verizon’s Data Breach Investigation Report, “76 percent of network intrusions exploited weak or stolen credentials.” Since vendors don’t need constant access to your network, they often use one remote access tool license and share generic logins and passwords across technicians. This makes the credentials easy for hackers to guess. What’s more, the vendor’s ex-employees often retain remote access to your systems.
Why is reducing network entry points important?
By reducing network entry points to the least amount that are necessary, you increase your ability to monitor and block unwanted activity on your network.
Can compromised servers be used to eavesdrop?
The National Institute of Standards and Technology (NIST) advises that compromised servers could be wielded to eavesdrop on and manipulate remote access communications. They can also provide a starting point for attacking other hosts within your organization.
Do third party vendors need access to network?
Third-party vendors should only need access to specific parts of your network. Your third-party vendor assessment should focus on access. Implement a least privilege policy covering who can access your data and network, and, specifically, what they can access.
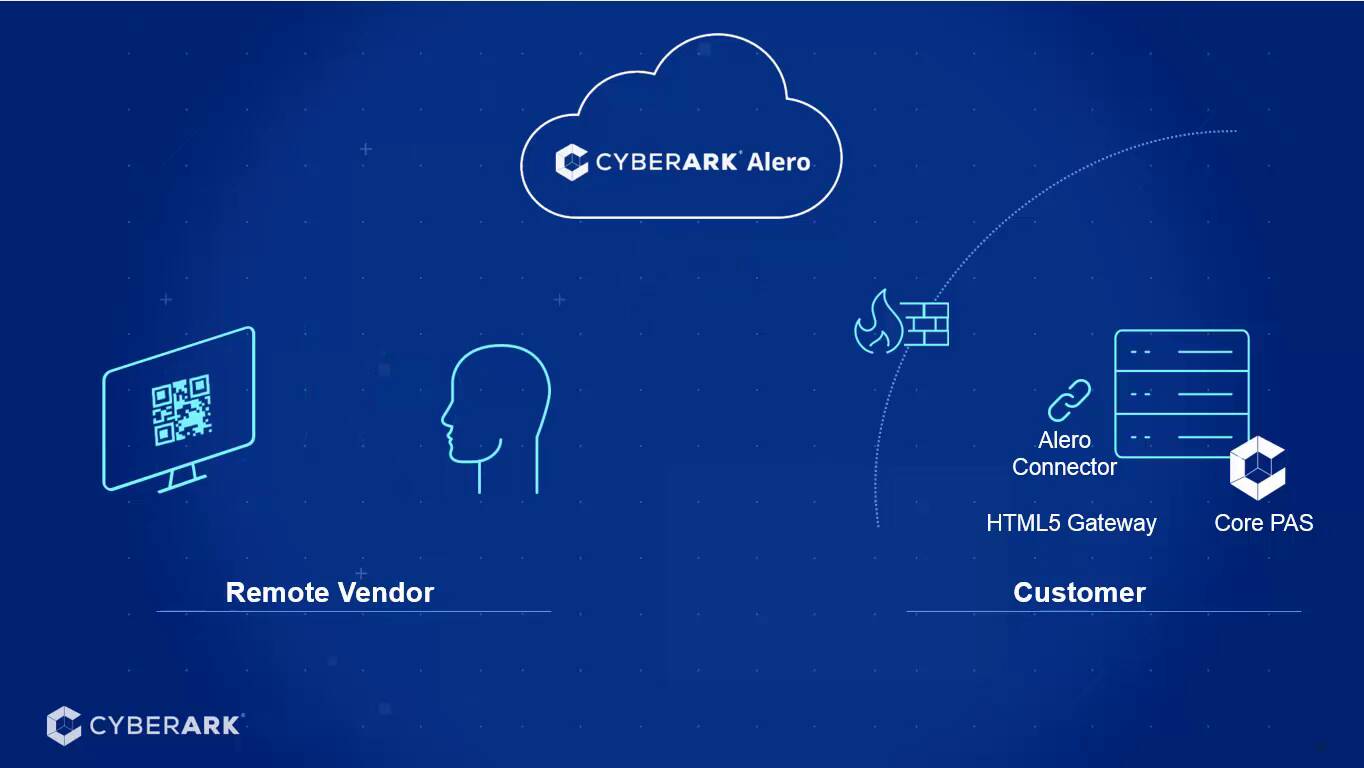
Vendor Privileged Access Manager Demo Video
CyberArk Vendor PAM gives the ability to invite, provision and give vendors privileged access. In this video, we'll show how to invite and give a vendor specific privileged access to a target system.
Vendor PAM Datasheet
Learn more about CyberArk Vendor PAM, a born in the cloud SaaS solution that helps organizations secure external vendor access to critical internal systems.
Vendor Privilege Access Management
Listen here for a 45 minute session on CyberArk Vendor PAM to provide external vendors with fast and secure access to critical systems managed within CyberArk PAM.
Remote Access Datasheet
CyberArk Remote Access helps organizations secure external vendor access to critical systems without the need for VPNs, agents or passwords.
Securing Remote Infrastructure: Keep Friends Close & Enemies Closer – Session 2 of 3
2020 has intensified demands around supply chains and external cloud services provision. This session looks at the IT Administration and Support teams, who continue to perform their duties remotely.
Enable New Ways of Work: Simplified Remote User Privileged Access with SaaS
Organizations everywhere are undertaking major digital transformation initiatives. Whether moving critical resources to the cloud, or investing in greater automation capabilities, COVID-19 has...
Time to Re-examine Remote Access After VPN Password Leak
Just days ago, a list of plaintext usernames, passwords and IP addresses for more than 900 Pulse Secure VPN servers was published online along with SSH keys for each server, a list of all local...
Why do vendors use multiple remote access tools?
Vendors often use multiple remote access tools because legacy tools can't meet all of their clients' needs, which can vary widely. Some require more advanced tiers of service while others have simpler or less frequent needs, impacting the way vendors need to interact with their various customers and systems.
What is the role of external vendors?
External vendors, outsourcers, and contractors play a vital and growing role in organizations, but when given access to your network and systems, they can be difficult to monitor and manage.
What are the risks of third party vendors?
According to Digital Shadows, there are three primary types of risks from third-party vendors: operational, transactional and compliance/regulatory. For your organization to prevent being impacted by these risk types, it is necessary to make sure the vendor’s security protocols are as close as possible to pre-remote work days. There should be an emergency plan, so you can continue with your business continuity if their security fails. Take the steps necessary to meet all compliance requirements for both industry and government standards.
Is third party vendor management a risk?
Third-party vendor management can be a risk to an organization’s data and network security. Enterprises depend on vendors to use security best practices that meet company standards while using their services when they have access to the company network. But that was when most people were working from their company’s physical place of business and there could be stricter cybersecurity oversight.
What is the line of defense for remote access?
So, you have a three-layer line of defense working to protect remote access to your network: anti-virus, firewall, and VPN. The network security team should monitor alerts from these defenses constantly.
What is remote access VPN?
The most basic form of VPN remote access is through a RAS. This type of VPN connection is also referred to as a Virtual Private Dial-up Network (VPDN) due to its early adoption on dial-up internet.
Why is IPSEC used?
This allows IPSec to protect data transmission in a variety of ways. IPSec is used to connect a remote user to an entire network. This gives the user access to all IP based applications. The VPN gateway is located at the perimeter of the network, and the firewall too is setup right at the gateway.
What is client side VPN?
The client-side software is responsible for establishing a tunneling connection to the RAS and for the encryption of data. RAS VPNs are appropriate for small companies, requiring a remote access for a few employees. However, most serious businesses have moved on from this basic form of VPN connection.
What do people use in an office?
Most, if not all, of the day-to-day tasks performed in offices today rely heavily on technology, mainly computers, laptops , tablets & smart devices. As the world and the global economy become increasingly interconnected, members of the staff too are required to go mobile. Sometimes, the need arises to work from home or somewhere away from the office, plus, a lot of companies have more than one office, in different parts of the world, and that requires them to have secure communications and exchange of data between offices.
Should a company use IPSEC VPN?
A company should go for IPSec VPN remote access if it has a strong networking department with the ability to configure each employee’s hardware device individually (installing client software, enforcing security policies etc.).
