Why is Splashtop a Better Choice than Legacy RDP / VPN?
| Splashtop | Traditional VPN / RDP | |
| Zero Trust Network Access (ZTNA) | Splashtop Yes (authentication is first e ... | Traditional VPN / RDP No (too much trust ... |
| Two-Factor Authentication (2FA/MFA) | Splashtop Yes | Traditional VPN / RDP Yes, but some MFA ... |
| Device Authentication | Splashtop Yes | Traditional VPN / RDP Not available in m ... |
- Zero trust network access. ...
- Secure access service edge (SASE) ...
- Software-defined perimeter. ...
- Software-defined wide area networks. ...
- Identity and access management and privileged access management. ...
- Unified endpoint management tools.
What is a VPN alternative and why do you need one?
Deploying a VPN alternative can enable an organization to improve visibility and security of their wide area network (WAN) while also increasing performance and teleworker productivity. What is a Virtual Private Network (VPN)? VPN solutions are designed to provide secure, remote access to an organization’s network.
What is a virtual private network (VPN)?
Virtual private networks (VPNs) are one of the most commonly used solutions for secure remote network connectivity. However, they have a number of limitations that negatively impact network performance and security.
Can virtual private networks be used to protect remote networks?
Virtual private networks have shortcomings when it comes to protecting remote network connections. These technologies can replace or supplement it. 7 VPN alternatives for securing remote... Top cybersecurity statistics, trends,...
Is ztna the answer to remote workplaces?
Remote users remain productive—and IT stays in control. When it comes to the digital workspace experience, traditional VPN and Zero Trust Network Access (ZTNA) technologies again fall short.

What can be used instead of VPN?
There are many models for accommodating remote work efficiently without compromising online security. A few alternatives to the VPN include virtual desktop infrastructure (VDI), The Onion Router (Tor), and proxy servers.
Do you need VPN for remote access?
A VPN will give you access to a network while remote desktop (or RDP) will give you control of an entire computer. If you want to have full control over a local computer from a remote location, VPN won't let you achieve that.
Which VPN is best for remote access?
Perimeter 81 – Best all-round business VPN. Jul 2022. ... GoodAccess – Security Strategy Options. Apps Available: ... ExpressVPN – Lightning Fast VPN. ... Windscribe – VPN with Enterprise-Friendly Features. ... VyprVPN – Secure VPN with Business Packages. ... NordVPN – Security-first VPN. ... Surfshark – VPN with Unlimited User Connections.
What is the difference between remote access and VPN?
A VPN is a smaller private network that runs on top of a larger public network, while Remote Desktop is a type of software that allows users to remotely control a computer. 2. Remote Desktop allows access and control to a specific computer, while VPN only allows access to shared network resources.
Is RDP better than VPN?
The biggest advantage of RDP is that you have access to network resources, databases, and line-of-business software applications without the limitations and high bandwidth demands of VPN. Because so little data passes through the connection, RDP is ideal for low-bandwidth environments.
Why would you use RDS instead of VPN?
VPN – Virtual Private Network encrypts your data and masks the IP address so that no malicious hacker can access the data and detect your location. The data is decrypted only at the intended destination. RDS – In RDS, the data is stored on the remote server and not on the end-point device.
Does ExpressVPN allow remote access?
To use VPN with a remote desktop, simply: Sign up for ExpressVPN and its blazing-fast and ultra-secure service. Connect to a server in a location that's closest to your remote desktop. Launch your remote desktop software and begin working!
How do you remotely access another computer?
Use Remote Desktop to connect to the PC you set up: On your local Windows PC: In the search box on the taskbar, type Remote Desktop Connection, and then select Remote Desktop Connection. In Remote Desktop Connection, type the name of the PC you want to connect to (from Step 1), and then select Connect.
Can I use NordVPN for remote desktop?
Unfortunately, you will not be able to use a remote desktop with NordVPN. Remote desktop service requires specific open ports and port-forwarding. Currently, we do not allow port-forwarding due to security reasons.
Is TeamViewer considered a VPN?
TeamViewer is the go-to VPN alternative with its end-to-end security measures like two-factor authentication, data encryption and whitelisting to ensure that sensitive information is extremely difficult to obtain.
Which method of remote access is the most secure?
Implement a Secure Connection for Remote Network AccessWired Connection: A wired connection is the most secure method for remote network access.Home Wi-Fi: The second most secure network connection is using a secured home Wi-Fi connection.More items...•
Is RDP better than VNC?
In general, Remote Desktop Protocol is known to be more functional and faster than VNC. However, both RDP and VNC can be the best option for different users with different purposes in mind.
What do you need for remote access?
Remote computer access requires a reliable internet connection. You'll need to activate or install software on the device you want to access, as well as on the device — or devices — you want to use to get that access.
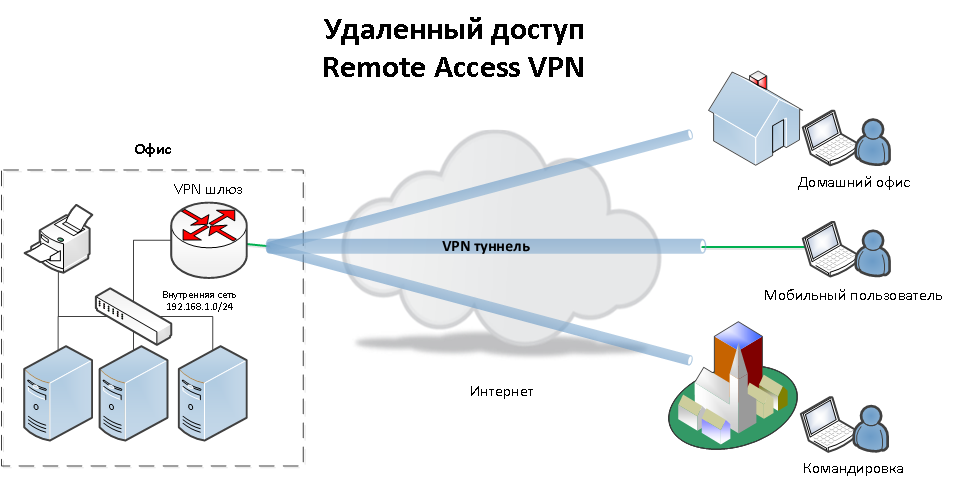
How does remote access work with VPN?
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
How do I access my work network remotely?
If you are a Windows use, go to Start→Accessories→Communications→Remote Desktop. Once you have reached the Remote Desktop, type in the name of your work computer then press "Connect." You should now be connected to your work computer and able to work from home.
What are the disadvantages of using a VPN?
The 10 biggest VPN disadvantages are:A VPN won't give you complete anonymity: Read more.Your privacy isn't always guaranteed: Read more.Using a VPN is illegal in some countries: Read more.A safe, top-quality VPN will cost you money: Read more.VPNs almost always slow your connection speed: Read more.More items...•
VPN pros and cons
VPN technology can be relatively inexpensive, especially with free or low-cost VPN packages. In these offerings, users simply access the VPN service, complete secure access procedures and enter the desired domain, such as a website address. More costly VPN technologies are likely to be used for large corporate networks.
1. Smart DNS
Smart DNS provides a proxy server resource for additional protection of a user's identity by masking a user's ISP-generated DNS address with a different address -- generated by the Smart DNS device -- before sending the user request into the internet.
2. The Onion Router
The Onion Router ( Tor) network protects user data by encapsulating the data in multiple layers of secure encryption -- using the Onion Protocol -- as it routes the data from sender to receiver. The Tor process ensures that a user's identity is protected from ISPs and advertisers.
3. Lantern
The Lantern network provides end-to-end security by encrypting all data traffic as it passes through Lantern servers. It differs from Tor in that it does not facilitate anonymity across the internet. It features higher-speed browsing and provides access to blocked websites and applications.
Planning considerations for VPN alternatives
The following are guidelines for planning a change in VPN technology or if the user is relatively new to VPNs:
What is VPN alternative?
VPN Alternatives for Business. Virtual private networks (VPNs) are one of the most commonly used solutions for secure remote network connectivity. However, they have a number of limitations that negatively impact network performance and security. Deploying a VPN alternative can enable an organization to improve visibility and security ...
What is VPN in business?
What is a Virtual Private Network (VPN)? VPN solutions are designed to provide secure, remote access to an organization’s network. They create an encrypted connection between the client – typically implemented as software on an employee’s computer – and a VPN gateway within the enterprise network. VPNs encrypt traffic flow between ...
Does VPN protect against malware?
A VPN provides no protection against malware, data exfiltration, or other security risks. Unless an organization has a full security stack deployed between the VPN and the enterprise network, infected remote machines can be used as a stepping stone to attack the enterprise network.
Is VPN a secure remote access solution?
As organization’s IT infrastructure increasingly moves off of the corporate LAN, VPN solutions are growing less effective as a secure remote access solution (especially for teleworkers working from mobile devices ). Secure SD-WAN and SASE provide a secure, high-performance alternative to legacy remote access solutions.
What is splashtop remote access?
Splashtop is designed to give users seamless, secure remote access to their computers from any device, e mbracing BYOD. With its industry leading remote desktop technology running through a secure SSL (AES-256) tunnel, Splashtop allows users to access their PC and Mac desktops via their Windows, Mac, iOS, Android, or Chromebook devices as if they are sitting in front of their computers or servers. You get all the benefits of RDP/VPN without the issues and complexities mentioned above. Also, it takes only minutes to set up.
What are the problems with RDP?
Common problems of using legacy remote access means through RDP over a VPN include: 1 The BYOD trend poses an increased security risk (60% of employees use a smartphone for work) 2 Difficulty setting up, maintaining, and scaling for more users 3 Poor user experience with connectivity and lag issues
Is VPN 24/7?
Dept of Homeland Security (DHS) warned, ” As VPNs are 24/7, organizations are less likely to keep them updated with the latest security updates and patches.” (March 13, 2020) No – Painful to setup and use VPN and RDP; VPN can take 20+ seconds to connect, and RDP is often slow. Corporate access uses corporate bandwidth.
Is RDP slow or human friendly?
User Productivity. Ease of Use. Splashtop. Click & connect – fast remote connections. Traditional VPN / RDP. No – Painful to setup and use VPN and RDP; VPN can take 20+ seconds to connect, and RDP is often slow .
Does splashtop use RDP?
Common problems of using legacy remote access means through RDP over a VPN include: Splashtop offers a RDP / VPN alternative solution that greatly simplifies remote access setup for IT and easy usability for employees/end-users.
What is SSO access?
A better option is seamless single sign-on (SSO) access that can be easily adapted based on individual device activity. This end-to-end contextual access ensures a superior employee experience without exposing your organization to unnecessary risk or creating privacy issues.
Does Citrix Gateway work with Citrix Secure Workspace?
Whether used on its own or integrated with Citrix Gateway, Citrix Secure Workspace Access provides access to all the apps and data your employees need—securely and reliably. Citrix Gateway customers can seamlessly integrate with Citrix Secure Workspace Access and start using our Workspace experience—unifying access to virtual apps and desktops, internal web apps, and SaaS apps—with the same granular security policies. For customers who have deployed Citrix Gateway for clientless VPN or SSO use cases, Citrix Secure Workspace Access provides additional security benefits.
Does remote work increase the risk of VPN attacks?
As remote work continues to rise, so does the number of exposed VPN services 1. Which is a concern, since traditional VPNs not only connect unmanaged devices to on-premises resources but also make trust implicit once network access is granted. The result is open connections, compromised assets, and an increased risk of network-level attacks.
SECURE REMOTE ACCESS
How work gets done has changed. VPNs can’t protect remote access at the scale demanded by your distributed IT and workforce. Zero Trust Network Access (ZTNA) empowers people to do their best work with quick, secure connections to anything from anywhere.
Zero Trust Network Access (ZTNA)
ZTNA offers major benefits over VPN alternatives. Many start their Zero Trust security journey with secure remote access as a first use case. This eBook examines how to cut enterprise risk and speed agility by replacing legacy VPN tech with robust ZTNA.
Ready for Secure Remote Access?
The Appgate team is available to answer questions, demo solutions and discuss secure remote access pricing. How can we help?
What is the function of a VPN?
The first fulfills a function analogous to that of a VPN: giving users access to the resources they need, avoiding exposing them to cyber threats. And the second is a firewall that protects users from malware infections, maintaining organization policies every time they connect to the Internet.
Why are VPNs important?
Connecting remote sites to a company’s network via the Internet always posed a significant security risk, as data sent from one site to another goes through public links and can be seen by malicious eyes. That is why VPNs were created as tunnels through which information circulates in an encrypted manner so that it cannot be intercepted and used by strangers.
What is the drawback of VPN?
Although the VPN creates a virtual and encrypted channel between users and an organization’s network, its drawback is that any breach that occurs in that channel gives potential attackers unlimited access to all resources connected to the organization network, which creates a risk of great proportions.
What is Zscaler private access?
Security-as-a-service company Zscaler offers a cloud-based zero-trust networking service — called Zscaler Private Access, or ZPA — that controls access to private applications, whether they run in public clouds or within a proprietary data center.