
- Update VPNs, network infrastructure devices, and remote employees’ devices with the latest patches and configurations.
- Implement multi-factor authentication on all VPN connections or otherwise use strong passwords.
- IT security personnel should test VPN limitations in preparation for mass usage.
- If possible, security personnel should use tools like rate limiting to prioritize users requiring higher bandwidths.
- Enable encryption. ...
- Install antivirus and anti-malware. ...
- Ensure all operating systems and applications are up to date. ...
- Enforce a strong password policy. ...
- Use Mobile Device Management (MDM) ...
- Use Virtual Private Network (VPN) ...
- Use two-factor authentication.
What are the best practices for securing remote access?
Best Practices for Securing Remote Access. RAS: The most basic form of VPN remote access is through a RAS. This type of VPN connection is also referred to as a Virtual Private Dial-up Network ... IPSec: IPSec is an IP packet authentication and encryption method. It uses cryptographic keys to protect ...
How to protect your network from remote access?
So, you have a three-layer line of defense working to protect remote access to your network: anti-virus, firewall, and VPN. The network security team should monitor alerts from these defenses constantly. Adopting two-factor authentication for remote access through VPN further boosts your network security.
How secure are VPNs?
While VPNs provide security by encrypting data and sending it through a “tunnel,” there are limitations to that security. Before examining those limitations, let’s take a look at how VPNs work.
Is it safe to use IPSec VPN for remote access?
A word of warning: If you are using IPSec VPN for remote access, but you are not deploying Internet Key Exchange (IKE, certificates) as an authentication method, the connection will be vulnerable. For many use cases, XAUTH and L2TP methods of IPSec authentication are prone to security lapses.
Why is IPSec VPN important?
Why is IPSEC used?
What is client side VPN?
What is IPSEC protocol?
What is remote access VPN?
What is the line of defense for remote access?
Should a company use IPSEC VPN?
See more
About this website
What are security requirements for remote access?
7 Best Practices For Securing Remote Access for EmployeesDevelop a Cybersecurity Policy For Remote Workers. ... Choose a Remote Access Software. ... Use Encryption. ... Implement a Password Management Software. ... Apply Two-factor Authentication. ... Employ the Principle of Least Privilege. ... Create Employee Cybersecurity Training.
What are the best practices in setting up a VPN?
Best practices for choosing and hardening a VPNSelect a standards-based VPN. ... Use a VPN with strong cryptography. ... Manage software vulnerabilities. ... Limit VPN access. ... Secure VPN traffic.
Is VPN remote access secure?
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
How do you secure remote access to a network?
Use virtual private networks (VPN) - Many remote users will want to connect from insecure Wi-Fi or other untrusted network connections. VPNs can eliminate that risk, however VPN endpoint software must also be kept up-to-date to avoid vulnerabilities that can occur from older versions of the software client.
How do I ensure security on VPN?
10 tips to secure client VPNsUse the strongest possible authentication method for VPN access. ... Use the strongest possible encryption method for VPN access. ... Limit VPN access to those with a valid business reason, and only when necessary. ... Provide access to selected files through intranets or extranets rather than VPNs.More items...•
How the security is maintained in VPN?
VPN security enables users to protect their online privacy and prevent their internet service provider (ISP) from tracking their browsing activity. It works by connecting a user's device to the VPN server, then passing their internet traffic through the VPN provider's internet connection.
What are the disadvantages of using a VPN?
The 10 biggest VPN disadvantages are:A VPN won't give you complete anonymity: Read more.Your privacy isn't always guaranteed: Read more.Using a VPN is illegal in some countries: Read more.A safe, top-quality VPN will cost you money: Read more.VPNs almost always slow your connection speed: Read more.More items...•
Which is more secure VPN or RDP?
Security. Although both VPN and RDP are encrypted through internet connection, a VPN connection is less accessible to threats than a remote desktop connection. For this reason, VPN is often considered more secure than RDP.
What is the difference between RDS RDP and VPN?
Unlike VPN, RDP typically enables users to access applications and files on any device, at any time, over any type of connection. The biggest advantage of RDP is that you have access to network resources, databases, and line-of-business software applications without the limitations and high bandwidth demands of VPN.
What are examples of remote user security policy best practices?
Best Practices For Remote Access SecurityEnable encryption. ... Install antivirus and anti-malware. ... Ensure all operating systems and applications are up to date. ... Enforce a strong password policy. ... Use Mobile Device Management (MDM) ... Use Virtual Private Network (VPN) ... Use two-factor authentication.More items...•
What are security considerations for remote users examples?
Five Remote Access Security Risks And How To Protect Against ThemWeak remote access policies. ... A deluge of new devices to protect. ... Lack of visibility into remote user activity. ... Users mixing home and business passwords. ... Opportunistic phishing attempts.
What are the secure methods the remote users can use to connect to the internal network to perform file operations?
VPNs are the most common form of remote access. They use authentication and encryption to establish a secure connection to a private network over the internet.
How do I setup a VPN on my router?
To enable the VPN feature:Launch an Internet browser from a computer or mobile device that is connected to your router's network.Enter the router user name and password. ... Select ADVANCED > Advanced Setup > VPN Service. ... Select the Enable VPN Service check box and click Apply.More items...•
Which VPN is the best?
The Best VPN Service for 2022NordVPN - Best VPN for Privacy.Surfshark - Best VPN for Security.Private Internet Access VPN - Best VPN for Windows.IPVanish - Best VPN for Android.Ivacy - Most Affordable.Atlas VPN - Best Data Breach Monitoring.ExpressVPN - Best Encryption.PureVPN - Best Server Base.More items...
What is VPN architecture?
VPN uses authentication methods, encryption algorithms, and other precautions to ensure that data sent between the two endpoints of its connection remains secure. VPN runs on the network layer of the TCP/IP layered communications stack model. Specifically, VPN uses the IP Security Architecture (IPSec) open framework.
How do you use a VPN?
Setting up a VPN in AndroidHead into Settings > Network & Internet > Advanced > VPN (you should see a little key icon). ... If you happen to be setting this up on a new phone, or if you haven't yet set a screen lock or password, Google will prompt you to first set one for your phone. ... Now create your VPN profile.More items...•
How to Secure Remote Access for Employees {Checklist}
How do you maintain security when employees work remotely, and your team is transitioning to a remote workforce? As remote work is becoming a more prevalent trend in business and considering the recent COVID-19 outbreak, there’s no better time for employees and companies alike to make strides in securing remote work.
What are the different types of VPNs?
There are basically four types of VPNs: 1 A firewall-based VPN is equipped with both a firewall and VPN capabilities. This type uses the security provided by firewalls to restrict access to an internal network and provides address translation, user authentication, alarms and logging. 2 A hardware-based VPN provides high network throughput as well as improved performance and reliability, but is also expensive. 3 A software-based VPN provides flexibility in terms of how traffic is managed. This is best for when endpoints are not controlled by the same party and when different firewalls and routers are used. 4 A secure socket layer (SSL) VPN enables users to connect to VPN devices using a web browser. SSL is used to encrypt traffic between the web browser and the VPN device.
How to improve VPN security?
Another way to improve VPN security is through perfect forward secrecy (PFS). If PFS is used, encrypted communications and sessions recorded in the past cannot be retrieved and decrypted should long-term secret keys or passwords be compromised.
What is software based VPN?
A software-based VPN provides flexibility in terms of how traffic is managed. This is best for when endpoints are not controlled by the same party and when different firewalls and routers are used. A secure socket layer (SSL) VPN enables users to connect to VPN devices using a web browser. SSL is used to encrypt traffic between ...
Which is better: OpenVPN or PPTP?
For those looking for the most secure, OpenVPN is the best. For those looking for support for many devices, PPTP may be the way to go. A VPN provides a means of accessing a secure corporate network over insecure public networks.
Why is a kill switch important?
The kill switch ensures that if the computer loses the VPN connection, either the Internet connection is shut down or the apps that are using the connection are shut down. This prevents the Internet address from being exposed.
What is VPN connection?
From the user’s perspective, the VPN connection is a point-to-point connection between the user’s computer and a corporate server. The nature of the public network is irrelevant to the user because it appears as if the data is being sent over a dedicated private link. As workers become more mobile, VPN connections allow users working at home ...
How does VPN work?
They operate on a principle of trusting whoever enters the network rather than using the principle of least privilege. The more secure ones are difficult to implement, as employees take time to put new security protocols in place, and VPNs overall are neither very flexible nor easy to manage.
Author: Haris Khan
Remote work is the new normal for IT teams around the globe, and there is no surprise as to why remote work is becoming so increasingly popular for organizations. The modern employee workforce is no longer restricted to one physical location.
What is secure remote access?
Secure remote access refers to the technology used for securely accessing a system or application remotely. Cybercriminals and malicious actors are consistently looking out for vulnerabilities and loopholes in remote work infrastructures to exploit and plan cyber attacks.
Which technologies are used for remote work access?
Secure remote access can be effectively implemented by utilizing a collection of highly innovative, secure, and flexible technologies while accessing a system or application from a remote location A few prominent examples of such technologies are listed below:
10 Best Practices for Secure Remote Work Access
Some of the best practices that you can adopt to improvise remote access security in your organization are described below:
Why cloud desktops are an optimal choice for secure remote access?
Cloud desktop solutions offer greater flexibility and ease of access as all of your files, applications and desktop reside on the cloud. Cloud desktops are one of the most resilient and secure forms of remote access.
All-In-One Secure Remote Access with V2 Cloud
As the organizational trend keeps transitioning to remote work, it’s crucial to comprehend the numerous cybersecurity risks and threats that are associated with remote access security. Remote work has become an increasingly viable option with tons of advantages.
Types of VPN Connections
To best support a client’s virtual private network connections, it is important to understand logical design and the difference between VPN clients and VPN gateways. Each client’s need will help determine which connection is best for the situation.
VPN Management Best Practices
As with most technical configurations, every managed service provider should follow a set of best practices while managing virtual private networks. These best practices cover both client and gateway management. Here are a few ideas.
VPN Protocol Selection
Several different protocols can be chosen for VPN encapsulation. Each has its advantages and it is important to understand what each offers when choosing what’s best to use.
Conclusion
For managed service providers to get ahead in the “new normal” of work environments, they must be able to provide their clients with virtual private networks that will meet their needs and keep their data safe. Having a deep understanding of how virtual private networks work and the best management practices is just the first step.
1. Enable encryption
Encryption is a tool designed to ensure the confidentiality and privacy of the data on your devices. Encryption mitigates the risks posed by a lost or stolen device. So even if a criminal were to gain physical access to any of your remote employees’ devices, the data on it would still be protected from unauthorized access.
2. Install antivirus and anti-malware
Antivirus and anti-malware software are required not just for security but also for regulatory compliance. Antivirus and anti-malware solutions provide a layer of protection where it is most needed, i.e. the users, who when in a rush or too busy tend to do stupid things that the IT team advises against.
3. Ensure all operating systems and applications are up to date
Software updates and patches are regularly released to improve the functionality, usability, or performance but more importantly, these patches often fix security vulnerabilities. If you delay updating your software, cybercriminals can use the known and yet unpatched vulnerabilities to hack into your system, install malware, or steal data.
4. Enforce a strong password policy
The use of weak passwords is an open invitation to cyber attacks. To safeguard your user accounts from cyber attacks, you need to enforce a strong password policy that helps create good password hygiene. You need to ensure that your password policy checks for length and complexity as well as disable automatic login, and enable automatic lock.
5. Use Mobile Device Management (MDM)
One of the key challenges of securing remote access is the difficulty of ensuring that the devices get the same level of security when they are remote as they would when in the office. This is where the Mobile Device Management (MDM) solutions help. MDM solutions allow you to monitor and manage devices wherever they are located.
6. Use Virtual Private Network (VPN)
While your employees work on the go, they may use public Wi-Fi at airports, hotels, or other public spaces. Therefore, you need to ensure that no one intercepts or snoops in while your employees are accessing the company resources from public Wi-Fi.
7. Use two-factor authentication
Two-factor authentication (2FA) provides excellent security, is relatively easy to implement, and comes at no extra cost. It is a type of multi-factor authentication, in which your username/password pair needs to be supplemented with another method such as an OTP (one-time-password) to verify your identity.
Why is IPSec VPN important?
IPSec VPN connections are also important for an employee who needs widespread access to the company’s network. A word of warning: If you are using IPSec VPN for remote access, but you are not deploying Internet Key Exchange (IKE, certificates) as an authentication method, the connection will be vulnerable.
Why is IPSEC used?
This allows IPSec to protect data transmission in a variety of ways. IPSec is used to connect a remote user to an entire network. This gives the user access to all IP based applications. The VPN gateway is located at the perimeter of the network, and the firewall too is setup right at the gateway.
What is client side VPN?
The client-side software is responsible for establishing a tunneling connection to the RAS and for the encryption of data. RAS VPNs are appropriate for small companies, requiring a remote access for a few employees. However, most serious businesses have moved on from this basic form of VPN connection.
What is IPSEC protocol?
IPSec: IPSec is an IP packet authentication and encryption method. It uses cryptographic keys to protect data flows between hosts and security gateways. The unique feature of IPSec is that it operates at the Network Layer of the Open Systems Interconnection (OSI) protocol model.
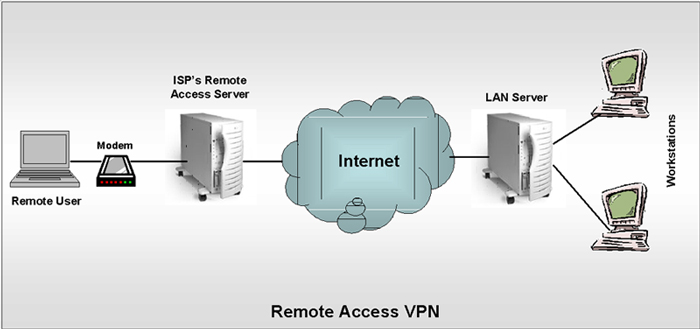
What is remote access VPN?
The most basic form of VPN remote access is through a RAS. This type of VPN connection is also referred to as a Virtual Private Dial-up Network (VPDN) due to its early adoption on dial-up internet.
What is the line of defense for remote access?
So, you have a three-layer line of defense working to protect remote access to your network: anti-virus, firewall, and VPN. The network security team should monitor alerts from these defenses constantly.
Should a company use IPSEC VPN?
A company should go for IPSec VPN remote access if it has a strong networking department with the ability to configure each employee’s hardware device individually (installing client software, enforcing security policies etc.).
