Types of encrypted VPNs
- Remote-access VPN: computer to network. A remote-access VPN extends almost any data, voice, or video application to a remote device, also known as an "endpoint" or a host.
- SSL VPN and IPsec. Secure Sockets Layer (SSL) VPN and IP security (IPsec) are tunnels and authentication technologies. ...
- Site-to-site IPsec VPN: network to network. ...
Full Answer
How to access remote computer via VPN?
Knowledge How do I remote into my computer at work from home using the VPN?
- Enable remote connection on your work computer. ...
- See How do I download and install the Cisco AnyConnect VPN client? ...
- Reboot your home computer
- After the reboot, go to your home computer's Windows Start Menu, search for Cisco AnyConnect VPN Client and open the program
- The AnyConnect window will come up and indicate that the VPN is "Ready to connect". ...
Why use a VPN for remote access in the cloud?
Why is a VPN Needed?
- Reduces Risk. A Clark School study is one of the first to quantify the near-constant rate of hacker attacks on computers with Internet access—every 39 seconds on average—and the non-secure ...
- Secures & Extends Private Network Services. ...
- Leverages Existing Security Investments. ...
- Increases Employee Productivity. ...
What is the difference between a VPN and remote control?
- Can access work-related assets
- Cheap
- Provides physical-level access to work computers
- Full encryption to protect against MITM attacks
- Stops prying eyes from your ISP or elsewhere
- Allows the employee to access geo-restricted content
What services can I access with VPN?
- Library databases (without logging in)
- All the information contained in PeopleFinder (without logging in)
- The MESA shared drive
- Remote into your office computer on campus
- Any other systems or resources your school or department restricts
- mason.gmu.edu server
What is the function of remote access VPN?
A remote access virtual private network (VPN) enables users who are working remotely to securely access and use applications and data that reside in the corporate data center and headquarters, encrypting all traffic the users send and receive.
What is a function of a remote access VPN CCNA?
A remote access Virtual Private Network (VPN) allows users working remotely to access and use applications and data residing in the corporate data center,headquarter offices, and cloud locations, often encrypting all user traffic.
What is VPN and its function?
VPN stands for "virtual private network" — a service that helps you stay private online. A VPN establishes a secure, encrypted connection between your computer and the internet, providing a private tunnel for your data and communications while you use public networks.
Do you need VPN for remote access?
No, but they serve a similar function. A VPN lets you access a secure network. RDP lets you remotely access a specific computer. Both will (usually) encrypt your traffic in one way or another, and both will grant you private access to a server or device that might be thousands of miles away.
What are important characteristics of remote access VPNs?
What is an important characteristic of remote-access VPNs?The VPN configuration is identical between the remote devices.Internal hosts have no knowledge of the VPN.Information required to establish the VPN must remain static.The VPN connection is initiated by the remote user.
Which VPN is best for remote access?
Perimeter 81 – Best all-round business VPN. Jul 2022. ... GoodAccess – Security Strategy Options. Apps Available: ... ExpressVPN – Lightning Fast VPN. ... Windscribe – VPN with Enterprise-Friendly Features. ... VyprVPN – Secure VPN with Business Packages. ... NordVPN – Security-first VPN. ... Surfshark – VPN with Unlimited User Connections.
When should you use a VPN?
Always use a VPN to encrypt any internet connection and help protect your data. Keep your VPN on when you wish to avoid bandwidth throttling. Sometimes ISPs tend to slow down users' traffic. This is because some ISPs do not have enough resources to cope with 24/7 streaming and gaming.
What is the difference between remote access and a VPN?
A VPN is a smaller private network that runs on top of a larger public network, while Remote Desktop is a type of software that allows users to remotely control a computer. 2. Remote Desktop allows access and control to a specific computer, while VPN only allows access to shared network resources.
How do I setup a VPN remote access?
Configure Remote Access as a VPN ServerOn the VPN server, in Server Manager, select the Notifications flag.In the Tasks menu, select Open the Getting Started Wizard. ... Select Deploy VPN only. ... Right-click the VPN server, then select Configure and Enable Routing and Remote Access.More items...•
What is remote access VPN vs site-to-site?
A remote access VPN connects remote users from any location to a corporate network. A site-to-site VPN, meanwhile, connects individual networks to each other.
What is VPN example?
VPNs are primarily used for remote access to a private network. For example, employees at a branch office could use a VPN to connect to the main office's internal network. Alternatively, a remote worker, who may be working from home, could need to connect to their company's internet or restricted applications.
How do I know if I have a VPN?
You can also navigate to your settings application, click network, and then see if you're running a VPN/proxy. Harder to check on Android/iPhone and doesn't really happen on the device. Check with your company's IT people to see if the WiFi is set up with a VPN/proxy.
How do I use VPN on my phone?
Open your phone's Settings app.Tap Network & internet. VPN. If you can't find it, search for "VPN." If you still can't find it, get help from your device manufacturer.Tap the VPN you want.Enter your username and password.Tap Connect. If you use a VPN app, the app opens.
When should I use a VPN on my phone?
The most typical scenario where you might use a VPN is if you're working remotely and using your laptop to connect to a specific private network, thus protecting your sensitive data.
What is VPN encryption?
In other words, your information that travels through the internet gets encrypted and encapsulated by a secure VPN gateway. This encryption technique plays a vital role in communicating your information to the remote destination. It scrambles your data and keeps it out of reach from notorious third parties like hackers and snoopers.
What happens after tunnel negotiation?
Once the tunnel negotiation gets over, the client can exchange encrypted communication with the remote gateway. After the encrypted data from the remote device reaches the remote gateway, it gets decrypted and shared with the internal or protected servers. Now, the remote server acknowledges the user through the remote gateway.
Why is remote access VPN important?
It also ensures to protect your online privacy. Remote access VPNs restrict user access to just one, which signifies the fact that it is designed for personal use. Nevertheless, if you are a digital nomad that remotely communicates with your organization’s network, remote access VPN could be the pick of the litter.
Which VPN supports remote access?
2) SSL VPN – Also known as mobile access VPN, SSL VPN supports only remote access connections. While both the blades offer an equal amount of data confidentiality, integrity and authenticity, let’s see the other features that differentiate each other. IPSec VPN. SSL VPN. Supports both TCP and UDP.
Is VPN clientless?
It is clientless and just requires a browser. Seamless to use. Not seamless, requires multilevel authentication. Other than the data security it offers, setting up a remote access VPN is cost-effective. With multiple VPN providers offering competitive business VPN plans, it also easy to upgrade your subscription plan as your business grows.
How does a NAS work?
Users connect to the NAS over the internet in order to use a remote access VPN. In order to sign in to the VPN, the NAS requires that users provide valid credentials. To authenticate these credentials, the NAS uses either its own authentication process or a separate authentication server running on the network .
What is remote access VPN?
What is a remote access VPN? Businesses use remote access VPNs to establish a secure connection between their network and the devices used by remote workers. Once connected, employees are able to access the resources on the network just as if their devices were physically plugged in at the office.
What is site to site VPN?
A site-to-site VPN uses a secure gateway to connect a network at one location to one or more networks at another location. This type of VPN doesn’t require each device at the end location to have a VPN client installed because the gateway handles the traffic.
Is remote access VPN secure?
Since remote access VPNs are affordable and secure, organizations can feel more comfortable with letting their employees work from home or while traveling.
Is VPN a security initiative?
Top VPN brands join security initiative. Ethics and VPN: the industry needs to aim higher. While VPNs have grown increasingly popular among users looking to protect their data and privacy online, using the right type of VPN can make all the difference when working remotely.
Where does Anthony live?
After living and working in South Korea for seven years, Anthony now resides in Houston, Texas where he writes about a variety of technology topics for ITProPortal and TechRadar. He has been a tech enthusiast for as long as he can remember and has spent countless hours researching and tinkering with PCs, mobile phones and game consoles.
What is remote access VPN?
What Is a Remote Access VPN? A remote access virtual private network (VPN) enables users who are working remotely to securely access and use applications and data that reside in the corporate data center and headquarters, encrypting all traffic the users send and receive. The remote access VPN does this by creating a tunnel between an ...
Why is VPN remote access?
The remote access VPN does this by creating a tunnel between an organization’s network and a remote user that is “virtually private,” even though the user may be in a public location. This is because the traffic is encrypted, which makes it unintelligible to any eavesdropper.
What are the advantages of using a SASE?
Some advantages of using a SASE are that it allows companies to: Apply security policies consistently across multiple locations and enforce least-privileged access. Simplify IT infrastructure and reduce costs by using a single cloud-based solution instead of having to buy and manage multiple point products.
Does SASE require a VPN?
Using SASE, an organization does not have to maintain a separate stand-alone proxy or VPN. Rather, users connect to a SASE solution (which provides access to the cloud and data center) with consistent security. Some advantages of using a SASE are that it allows companies to:
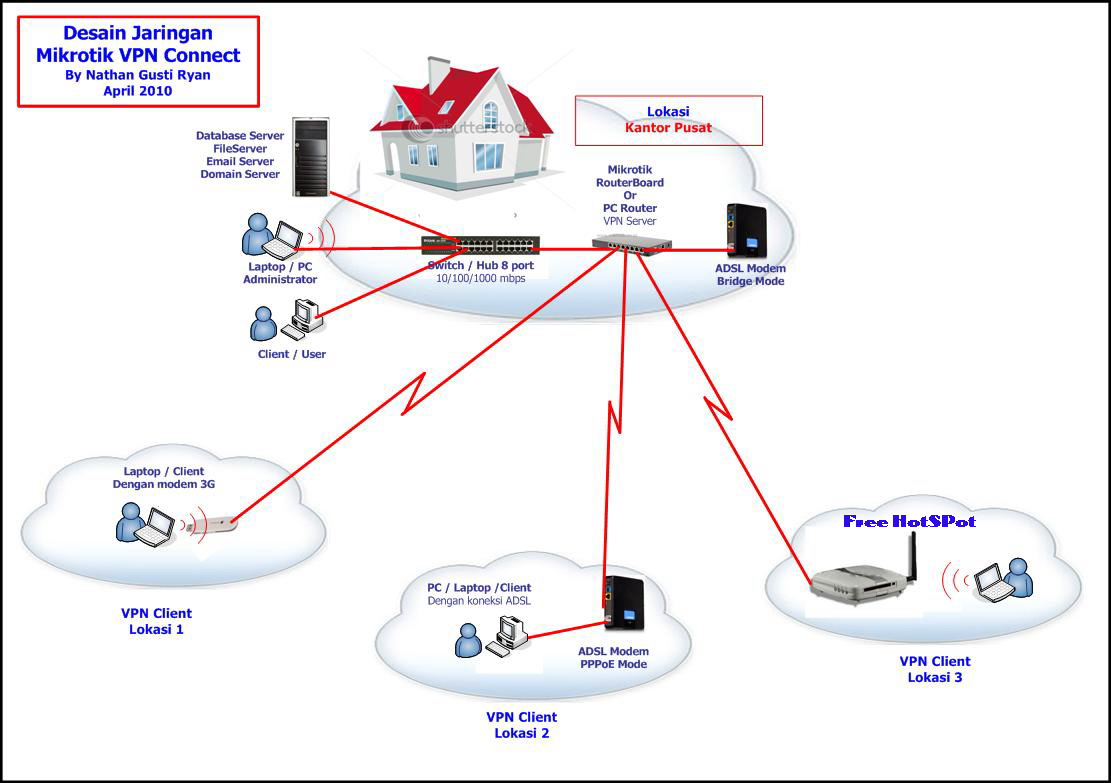
What is a VPN topology?
A VPN topology specifies the peers and networks that are part of the VPN and how they connect to one another. Here is a quick overview of the three main types of topologies: Hub-and-spoke. In this VPN topology, multiple remote devices (spokes) communicate securely with a central device (hub).
What is SSL VPN?
Secure Sockets Layer (SSL) VPN and IP security (IPsec) are tunnels and authentication technologies. Businesses can use SSL VPN, IPsec, or both to deploy a remote-access VPN, depending on deployment requirements. SSL VPN and IPsec protect data traversing the VPN from unauthorized access.
What is IPsec policy?
An IPsec policy defines the characteristics of the site-to-site VPN, such as the security protocols and algorithms used to secure traffic in an IPsec tunnel. After an organization creates a VPN topology, it can configure the IPsec policies it applies to that topology, depending on the assigned IPsec technology.
What is VPN in business?
A virtual private network (VPN) extends a company's network, allowing secure remote user access through encrypted connections over the Internet. This allows VPN traffic to remain private as it travels between devices and the network. As a VPN user browses the web, their device contacts websites through the encrypted VPN connection.
What is secure remote access?
Secure remote access is a method for connecting remote users and devices securely to a corporate network. It includes VPN technology, which authenticates users or devices, confirming that they meet certain requirements—also known as "posture"—before they can connect to the network remotely.
What is a partial mesh VPN?
This is a network in which some devices are organized in a full mesh topology, and other devices form either a hub-and-spoke or a point-to-point connection to some of the fully meshed devices.
What is split tunneling?
Split tunneling occurs when a device on the remote end of a VPN tunnel simultaneously exchanges network traffic with both the public and private networks without first placing all the network traffic inside the VPN tunnel.
What is remote access VPN?
A remote access Virtual Private Network (VPN) allows users working remotely to access and use applications and data residing in the corporate data center,headquarter offices, and cloud locations, often encrypting all user traffic.
How do remote access VPNs work?
Remote access VPNs create virtually 'private' tunnels between an organization's network and a remote user, regardless of the user's location.
Why are remote access VPNs becoming obsolete?
The days of network-centric security are over. For almost three decades, enterprises have relied on castle-and-moat methods to connect users to the network, and by extension, the applications running on it.
Why is a SASE approach better than remote access VPN?
SASE is a framework identified by Gartner as the way to securely connect entities such as users and devices to applications and services when their locations may be anywhere.
Why is zero trust network access (ZTNA) preferred over remote access VPN?
Zero trust network access (ZTNA) takes a user- and application-centric approach to private application access, ensuring that only authorized users have access to specific private applications by creating secure segments of one between individual devices and apps. That means no more network access, no more lateral movement.
What is Zscaler Private Access (ZPA)?
Zscaler Private Access (ZPA) is a cloud service from Zscaler that provides seamless, zero trust access to private applications running on the public cloud or within the data center. With ZPA, applications are never exposed to the internet, making them completely invisible to unauthorized users.
Why is ZPA superior to remote access VPN?
In contrast to VPN, ZPA is a more modern, robust security solution offering the following benefits: