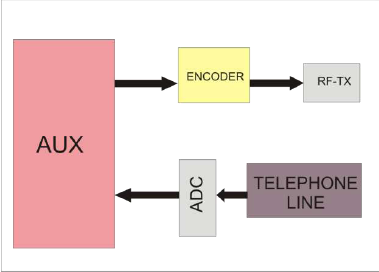
What is a remote access device? Remote access (or remote desktop) is the ability to access a computer or device from another device, at any time, and from anywhere. Can Windows 10 Remote Desktop to Windows XP? Yes Remote Desktop connection in Windows 10 will work to connect to Windows XP if and only if it is of professional edition.
Does Someone have remote access to my computer?
You can detect remote access on your computer by identifying the software programs currently in use and recognizing any abnormalities. If you have ever wondered "Is someone else controlling my computer," you are not alone.
Can someone help me with remote access?
Windows Remote Assistance lets someone you trust take over your PC and fix a problem from wherever they are. Before you can use it, you'll need to enable access. In the search box on the taskbar, type remote assistance, and then select Allow Remote Assistance invitations to be sent from this computer from the list of results.
How secure is enabling remote access?
- iOS/Android: Swap album and artist titles in CarPlay/Android Auto.
- iOS/Android: Rare crash if your library had ~200,000 items.
- Desktop: Reduce hover play background size to allow clicking on poster.
- iOS: Crash for high CPU in some cases if server disks were offline.
- CarPlay/Android Auto: Show all albums when album types are enabled.
How do I know if remote access is enabled?
- Go back to System Preferences and click Security & Privacy.
- Click the Firewall tab.
- Click Firewall Options or Advanced.
- If “Remote Management” doesn’t appear in the box with the phrase “Allow incoming connections,” click the + to add it, and then select Allow incoming connections.

What is remote access examples?
Accessing, writing to and reading from, files that are not local to a computer can be considered remote access. For example, storing and access files in the cloud grants remote access to a network that stores those files. Examples of include services such as Dropbox, Microsoft One Drive, and Google Drive.
How does a remote access work?
Remote access simply works by linking the remote user to the host computer over the internet. It does not require any additional hardware to do so. Instead, it requires remote access software to be downloaded and installed on both the local and remote computers.
Can you tell if someone is remotely accessing your computer?
You can use the Windows Task Manager on your computer to assess whether any programs have been opened on your computer without your knowledge. If you see programs in use that you did not execute, this is a strong indication that remote access has occurred.
Can someone control my computer remotely?
For any attacker to take control of a computer, they must remotely connect to it. When someone is remotely connected to your computer, your Internet connection will be slower. Also, many times after the computer is hacked, it becomes a zombie to attack other computers.
Is remote access safe?
Remote access solutions could leave you vulnerable. If you don't have proper security solutions in place, remote connections could act as a gateway for cybercriminals to access your devices and data. Hackers could use remote desktop protocol (RDP) to remotely access Windows computers in particular.
How do I trace remote access?
1:132:22How to trace remote access logs VPN access - YouTubeYouTubeStart of suggested clipEnd of suggested clipAnd I'm just gonna type in C colon backslash Windows backslash tracing and that's gonna open up myMoreAnd I'm just gonna type in C colon backslash Windows backslash tracing and that's gonna open up my tracing directory.
Is my phone being remotely accessed?
Signs That Someone Has Remote Access to Your Phone The battery drains quickly even when not in use. Higher data usage than usual. Noises in the background when you're on a phone call. You receive unusual messages, emails, or notifications.
Can someone remotely access my computer with my IP address?
Someone can use your IP to hack your device The internet uses ports as well as your IP address to connect. There are thousands of ports for every IP address, and a hacker who has your IP can try all of those ports to brute-force a connection, taking over your phone for example and stealing your information.
Can hackers see my screen?
Ang Cui from Red Balloon Security has figured out a way to hack into a popular Dell monitor and manipulate what you see on your screen. Using this type of attack, a user could easily be tricked into revealing personal, private information.
What happens when a hacker gets remote access to my computer?
Hackers use RDP to gain access to the host computer or network and then install ransomware on the system. Once installed, regular users lose access to their devices, data, and the larger network until payment is made.
How can I tell if my computer is being monitored at work 2022?
Open task manager by right-clicking on the taskbar and choosing Task Manager. If there's a suspicious process, that's the monitoring app. Question: Can my company see what I do on my computer? Answer: Your company can see your device activities and track them if they provide you with that computer.
How can I tell if my computer is being monitored at work 2022?
Open task manager by right-clicking on the taskbar and choosing Task Manager. If there's a suspicious process, that's the monitoring app. Question: Can my company see what I do on my computer? Answer: Your company can see your device activities and track them if they provide you with that computer.
How do I see who is connected to my computer?
right click on my computer -> manage ->shared folders -> sessions/open files. that will tell you what windows shares they are looking at.
What is remote access?
Remote access is the ability for an authorized person to access a computer or network from a geographical distance through a network connection.
How does remote access work?
Remote access is accomplished with a combination of software, hardware and network connectivity.
What are the types of remote access?
Traditionally, enterprises used modems and dial-up technologies to allow employees to connect to office networks via telephone networks connected to remote access servers. Devices connected to dial-up networks use analog modems to call assigned telephone numbers to make connections and send or receive messages.
What is remote access?
Remote access, also known as remote login, is the ability to access the data stored on a computer from a remote location. It enables you to open, edit, and save files located on your device from anywhere in the world. This ability is handy for offsite workers, travelers, and those who work out of office. There are several ways to set up remote ...
How does remote access work?
Remote access works by utilizing software, hardware, and network configurations. . Despite the recent uptick in trend, this isn’t a new concept. In fact, it was even possible to access remote files before the advent of the internet.
What is VPN for branch offices?
VPN itself was specifically developed for remote employee access and interconnectivity between branch offices. It provides a way to securely and remotely access resources on company servers with verified login credentials. Remote access works by utilizing software, hardware, and network configurations. .
Why do we need remote access protocol?
It also helps keep your server secure and protected against hacks and leaks. There are several protocols for doing this:
Why is remote access important?
Remote access also ensures that a company can hire whoever they want without the need for relocation. They can work with the best in the industry, no matter where they live, cutting out geographical restraints for both employees and employers. Another benefit is the easy availability of technical support.
Can I access my cloud files remotely?
The cloud has made it easy to access these files from anywhere. However, if you haven’t backed up your device recently or transferred data onto the cloud, you won’t be able to access files remotely. Remote access allows you to open and edit files when your computer is out of reach. It can also be helpful in the case of lost, stolen, ...
Can employees access a server in the office?
Employees can access a single server in the office when they’re out of town or the weather permits them from coming in. You could be at a conference and access the resources needed for a presentation or pull up important notes for an unexpected networking opportunity.
What is remote access?
Remote access is the act of connecting to IT services, applications or data from a location other than headquarters or a location closest to the data center. This connection allows users to access a network or computer remotely via an internet connection or telecommunications. Secure remote access benefits include: ...
Why is remote access important?
It is valuable for businesses to have a strategy for allowing remote access to their users.
Why is it important to have a bring your own device?
With remote access, data stays secure and workers can be productive at any location. By allowing employees to use their own device, businesses can exponentially lower the costs of purchasing and managing corporate-owned devices.
What is Citrix Networking?
With Citrix Networking and SmartAccess, organizations have the capability to control printers, client devices, session connectivity, and reactive security postures. Admins are also able to leverage the full capabilities of Citrix Analytics to collect data for improving app performance, supporting continuous operations, and enhancing security.
Why is remote access important?
Remote access software is helpful when you’re in a meeting at another office with your laptop — or telecommuting — and need an important file that’s on your office computer. Remote computer access can help you assist someone in your personal life who might be far away.
How to protect your computer when using remote access?
Here are some steps you can take to help protect your computer and data while relying on remote access. Maintain strong passwords.
Is there a third party remote access program?
For instance, there are Windows-only and Mac-only programs if your computers and devices all use the same operating system.
Can hackers use RDP?
Hackers could use remote desktop protocol (RDP) to remotely access Windows computers in particular. Remote desktop servers connect directly to the Internet when you forward ports on your router. Hackers and malware may be able to attack a weakness in those routers.
What is remote access?
Have you ever left home and wished that you had a copy of your resume? Or maybe you wanted to show someone that cute baby video? Or suppose you want to login to your home desktop computer from the Bahamas and run maintenance programs on your PC while you’re sipping on two-for-one margaritas at the beach.
What are the benefits of using remote access?
After you setup remote access to your network, you can do a lot of really cool stuff, for example:
What do I need to enjoy remote access?
For starters, you’ll need to serve the requests coming into your network. Then, you’ll need to route those requests through your network.
What is DDNS and how does it work?
Dynamic DNS (DDNS) is particularly helpful in residential home networks whereby the ISP issues a public IP address that changes dynamically without notice. DDNS takes a domain name such as www.yourdomain.com and associates it with your public IP address. It also updates your public IP address at predefined intervals (say, every 7, 14, or 28 days).
What choices do I have for obtaining a domain name?
You can get a free or paid domain name. Free domains aren’t really yours. They’re typically identified by a hostname or username, followed by a domain name. I prefer having a paid domain because I like the additional flexibility and choice of what my domain name looks like. With a free domain name, your address will look something like this:
How do I forward requests through my network?
Ok, now that we can serve requests coming “to” our network, let’s talk about how to forward those requests “through” our network.
What is Port Forwarding?
The first time I heard the term “port forwarding” I thought it was something straight out of a Star Trek movie, or something reserved for “left-brain” people (you know… smart folks). I soon learned that this “Poindexter” stuff wasn’t so intimidating after all.