Remote policies have guidelines for access that can include the following:
- Hardware and software configuration standards for remote access, including anti-malware, firewalls, and antivirus
- Encryption policies
- Information security, confidentiality, and email policies
- Physical and virtual device security
- Access privileges, authentication, and access hierarchy
- Connectivity guidelines
- Password protocols
- Acceptable use policies
Full Answer
Who does the remote access policy apply to?
This policy applies to all, faculty, and staff of Cambridge College who require remote access to the College network while away from their office. These users are responsible for reading, understanding, and complying with this policy.
What is the Cambridge College remote access policy?
The policy's guiding philosophy is to keep Cambridge College information within the Cambridge College internal network. As such, this policy is designed to enable users' full remote access to authorized resources that are necessary to perform their jobs while minimizing the exposure of College IT resources to external threats.
What is the purpose of the remote working policy?
As such, this policy is designed to enable users' full remote access to authorized resources that are necessary to perform their jobs while minimizing the exposure of College IT resources to external threats.
What is a remote access policy (rap)?
What Is a Network Security Policy? A remote access policy is commonly found as a subsection of a more broad network security policy (NSP). The network security policy provides the rules and policies for access to a business’s network.
What is in a remote access policy?
A remote access policy serves as a guide for remote users connecting to the network. It extends the policies governing network and computer use in the office, e.g., password policy.
Why is a remote access policy important?
A remote access policy is vital to ensure that your organization can maintain its cybersecurity protocols even with all the uncertainty that remote access brings: unknown users (you can't see the person, after all), using potentially unknown devices on unknown networks, to access your corporate data center and all the ...
What is the meaning of remote access?
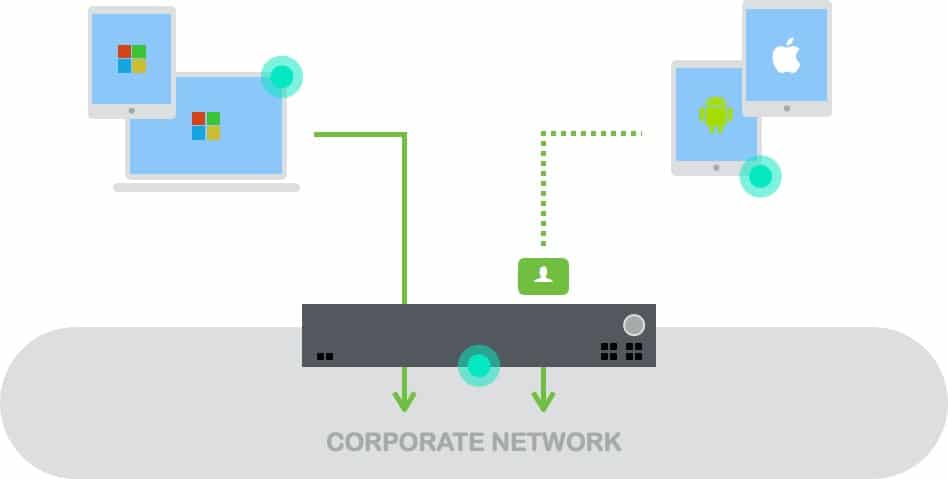
Remote access is the act of connecting to IT services, applications, or data from a location other than headquarters. This connection allows users to access a network or computer remotely via the internet.
What is remote access examples?
Accessing, writing to and reading from, files that are not local to a computer can be considered remote access. For example, storing and access files in the cloud grants remote access to a network that stores those files. Examples of include services such as Dropbox, Microsoft One Drive, and Google Drive.
Is IT safe to allow remote access?
Remote access solutions could leave you vulnerable. If you don't have proper security solutions in place, remote connections could act as a gateway for cybercriminals to access your devices and data. Hackers could use remote desktop protocol (RDP) to remotely access Windows computers in particular.
How do I restrict remote access to my computer?
Open System and Security. Choose System in the right panel. Select Remote Settings from the left pane to open the System Properties dialog box for the Remote tab. Click Don't Allow Connections to This Computer and then click OK.
What are the types of remote access?
The primary remote access protocols in use today are the Serial Line Internet Protocol (SLIP), Point-to-Point Protocol (PPP), Point-to-Point Protocol over Ethernet (PPPoE), Point-to-Point Tunneling Protocol (PPTP), Remote Access Services (RAS), and Remote Desktop Protocol (RDP).
What are the benefits of remote access?
Here, we discuss the most common flexible working benefits that can be supported by your remote access strategy.A more productive workforce. ... Better talent acquisition. ... IT support from anywhere. ... Improved security for remote workers. ... Lower overhead cost. ... Business continuity planning.
What happens if you give someone remote access to your computer?
This can be even worse than just conning you out of money, as undetected malware can allow hackers to steal your identity, including your passwords and financial information, over and over again, even if you get new passwords and account numbers.
Can someone remotely access my computer without my knowledge?
"Can someone access my computer remotely without me knowing?" The answer is "Yes!". This could happen when you are connected to the internet on your device.
What is the greatest benefit of remote access to an organization?
Flexibility. By allowing your staff to perform tasks outside the office using remote access, you can facilitate more flexible work arrangements and help employees create a better work/life balance.
What is the purpose of a password policy?
A password policy is a set of rules designed to enhance computer security by encouraging users to employ strong passwords and use them properly. A password policy is often part of an organization's official regulations and may be taught as part of security awareness training.
What is an access policy?
n. Principles or procedures that control the conditions under which individuals have permission and ability to consult a repository's holdings.
What is remote access policy?
Remote access policies are an ordered set of rules that define how connections are either authorized or rejected. For each rule, there are one or more conditions, a set of profile settings, and a remote access permission setting. If a connection is authorized, the remote access policy profile specifies a set of connection restrictions. The dial-in properties of the user account also provide a set of restrictions. Where applicable, user account connection restrictions override the remote access policy profile connection restrictions.
How to verify remote access server?
1. Either use the Rqc.exe notification component or create a notification component that provides verification to the remote access server that the remote access client computer complies with network policy requirements. 2. Create a validation script that authorizes the client configuration.
How to enable EAP authentication?
Follow these steps to enable EAP authentication:#N#1.#N#Select Start | Administrative Tools | Internet Authentication Service.#N#2.#N#The IAS management console is displayed. Click to highlight Remote Access Policies in the left column.#N#3.#N#In the right column, select Connections to Microsoft Routing and Remote Access Server .#N#4.#N#Select Action | Properties from the menu, or right-click and select Properties from the context menu. #N#5.#N#The Properties dialog box is displayed. Click the Edit Profile button .#N#6.#N#The Edit Dial-in Profile dialog box is displayed. Select the Authentication tab.#N#7.#N#The authentication methods supported by IAS are displayed, as shown in Figure 5.14. You can enable or disable the non-EAP authentication methods here. You can also change the order in which the selected EAP types are negotiated by moving them up or down in the list, using the Move Up and Move Down buttons.#N#Sign in to download full-size image#N#Figure 5.14. Authentication Methods#N#8.#N#Click the EAP Methods button. A list of the currently enabled EAP types is displayed.#N#9.#N#Click Add and select MD5-Challenge from the list.#N#10.#N#Click OK, then click OK in the EAP types list.#N#11.#N#Click OK to exit the Edit Profile dialog box.#N#12.#N#Click OK to exit the Properties dialog box.
How to enable EAP on IAS?
To enable EAP authentication on an IAS server, you create a Remote Access Policy that allows EAP authentication, or you modify an existing policy. Exercise 5.07 demonstrates how to modify a policy to allow the use of MD5 CHAP authentication through EAP.
How to delete VPN policy?
You can delete the other policies if you require only VPN connections to your ISA firewall. Right-click on Connections to other access servers, and click Delete. Repeat with Connections to Microsoft Routing and Remote Access server.
What is VPN quarantine in Windows 2003?
A new feature that comes with a new set of utilities for Windows Server 2003 is Network Access Quarantine Control. Using either the Connection Manager Administration Kit (CMAK) or the Windows Deployment and Resource Kits, administrators can configure special policies that restrict VPN client access using a quarantine mode until the client system is either brought into compliance with corporate VPN client specifications or determined to already be in accordance with specifications. This is a new feature for Windows Server 2003 that will help to increase network security.
What is PPP protocol?
The official implementation, as used by Microsoft, comes from RFP 1990. Capabilities were added and subsequent modifications to the standard were made leading up to PPP as it exists today. In 1994, a documented standard was proposed for “The PPP Multilink Protocol” in RFC 1717. At the time, other proposals existed to combine streams of data at the bit level (basically a hardware solution). This proposal described a software-based solution for the need to combine multiple streams of data into one. This solution was well-suited to the twin bearer channels of ISDN (2B+D).
What is remote access policy?
A remote access policy is a document that details how an employee can safely connect to a company's computer network while working away from the office.
Which university publishes remote access policy?
For example, Appalachian State University in North Carolina publishes its remote access policy online. In it, among other things, they detail:
Should you mention password policies in remote access policy?
Last, if you reference other policies or standards you have implemented in your company's security program in your remote access policy, you should make mention of those so they can be reviewed. A strict password policy that your organization requires of its employees should be noted.
Can you work remotely from home?
Let's face it. Technology today allows employees to work from just about anywhere. Whether you are a full-time telecommuter who works from a home office or you just need a break from the usual scenery and head off to a coffee shop, the ability to work remotely is a definite perk of the 21st century.
What is remote access?
Remote access refers to the process of connecting to internal resources from an external source (home, hotel, district, or other public area). The ability to securely and reliably connect to business resources from a remote location increases productivity.
Who bears full responsibility for any access misuse?
Users shall bear full responsibility for any access misuse
What is LEP password policy?
All user passwords shall be strong and follow guidelines and procedures in the [LEP] Access Control and Password Policy. Staff shall ensure that devices used for work purposes are not shared in a multi-user capacity, violate AUP conditions, or used in any inappropriate activity.
What is information security?
Information security shall determine the appropriate access methodology and hardening technologies up to and including two factor password authentication, smart card, or PKI technology with strong passphrases
What is LEP policy?
This policy defines standards for staff to connect to the [LEP] network from a remote location. These standards are designed to minimize potential exposures including loss of sensitive information, and limit exposure to security concerns through a consistent and standardized access method.
What happens if a staff member is found in a policy violation?
Staff members found in policy violation may be subject to disciplinary action, up to and including termination.
Can you use personal equipment to connect to a LEP network?
Personal equipment shall not be used to connect to the [LEP] network using remote connection software and exceptions require [Insert Appropriate Role] written approval
How to secure remote access?
Remote access must be secured and strictly controlled with encryption by using firewalls and secure 2FA Virtual Private Networks (VPNs).
Why is remote access important?
Remote access to your corporate IT infrastructure network is essential to the functioning of your business and the productivity of the working unit. There are external risks that must be mitigated to the best of your ability by designing a secure access policy and implementing ISO compliance controls. The purpose of the policy defines and states the rules and requirements for accessing the company’s network. Rules must be defined to eliminate potential exposure due to unauthorized use, which could cause a loss of the company’s sensitive data and intellectual property, a dent in its public image, and the compromise of resources. Here are the guidelines for defining the rules to eliminate potential exposure due to unauthorized use:
Why should firewall operation mode be stateful?
The firewall operation mode should be configured as stateful rather than stateless, in order to have the complete logs.
What is the responsibility of a user in a corporate network?
The user should be completely responsible to ensure not to violate any of the organization’s policies, and that he does not perform illegal activities, and does not use the access for outside business interests while accessing the corporate network remotely.
How many people work remotely?
A study by one Switzerland-based service office provider says that 70% of people globally work remotely at least once a week, and so telecommuting is more popular than ever.
Is remote access to the organization's network a risk?
Giving your employees the possibility to work from anywhere has myriad advantages, but measures of wariness need to be taken. This is why remote access to the organization’s network needs to be interpreted as a risk, and hence there is a need to have appropriate controls for it. Therefore, it should be allowed only in the cases where required and with adequate security controls required by ISO 27001.
Should remote access be limited?
The abilities of remote access users should be limited by allowing only certain operations to users, and there should be a policy for removal of authority and access, along with the return of equipment when the teleworking activities are terminated or no longer required.
Who must obtain prior approval from Information Security Office for remote access to Connecticut College?
4.3.6 Organizations or individuals who wish to implement nonstandard Remote Access solutions to the Connecticut College production network must obtain prior approval from Information Security Office
Who approves exceptions to the policy?
Any exception to the policy must be approved by the Chief Information Security Officer in advance.
What is the purpose of the Connecticut College network policy?
These standards are designed to minimize the potential security exposure to Connecticut College from damages which may result from unauthorized use of Connecticut College resources. Potential damages include the loss of sensitive or college confidential data, intellectual property, damage to public image, and damage to critical Connecticut College internal systems.
What is an academic VPN?
a. Academic VPN allows all valid employees and students to access the College network resources.
What is the responsibility of Connecticut College employees, students, and College Affiliates?
It is the responsibility of Connecticut College employees, students, and College Affiliates with remote access privileges to Connecticut College's campus network to ensure that their remote connection is given the same information security consideration as the user's onsite connection to Connecticut College.
Why Is a Remote Access Policy Necessary?
The numerous types of mobile devices and the different ways to connect pose challenges for the IT department. Devices can include cell phones, tablets, laptops, and any other device a remote worker relies on to conduct business. They can be company owned and secured, personally owned and authorized by a Bring Your Own Device (BYOD) policy, or a combination. Each class of device has its own set of security challenges. According to the National Institute for Standards and Technology’s Guidelines for Managing the Security of Mobile Devices in the Enterprise, “…Security controls available for laptops today are quite different than those available for smartphones, tablets, and other mobile device types.” Since different devices demand different controls, the policy has to detail what is allowed, compliant, and secure. The policy should answer the following questions:
What Is Remote Access?
Remote access is any connection made to an organization's internal network and systems from an external source by a device or host. Remote locations can be almost anywhere in the world, from the employee’s home to an off-site office, hotels, transportation hubs, and cafes.
What Problems Arise Without a Remote Access Policy?
Therefore, consequences for misuse can also be clearly outlined to compel compliance and appropriate precautions for data use and access. Elements such as firewalls, connectivity guidelines, personal use restrictions, and antivirus updates can help IT prevent both malicious and accidental loss and disruption of corporate information assets. The remote access control policies also provide protections for confidentiality, intellectual property, and information compliance.
What is VPN policy?
Policies for VPN remote access can be standardized. These policies “shore up” and prevent the use of rogue devices and access by non-authorized users , including the worker's family members or housemates. The policy also enforces proper email protocols to protect information from being sent through unsecured or untrusted sources, and also provides rules that limit or prohibit split tunnel configurations that allow mobile users to access both secure and unsecure networks simultaneously.
What is telecommuting?
“Telecommuting,” a term coined in the 1970s, has experienced explosive growth in today’s era of mobile connectivity. Now called distributed offices, remote work, telework, mobile work, smart work, and work shifting, many people are finding flexibility and increased productivity conducting business away from a centralized office environment. Researchers have long studied the benefits of remote work - from the successes that remote work had on traffic reduction during the 1984 Los Angeles Olympics to the 2016 findings by a Gallup survey on the increased hours for remote work.
What percentage of people work remotely?
According to research conducted by Gallup, 43 percent of workers in the U.S. worked remotely at least some of the time in 2016. Remote workers report higher job satisfaction and flexibility, experience fewer distractions and interruptions, and are more productive. Companies experience less absenteeism, less stress on office accommodations, and realize greater employee retention. A recent New York Times article found that finance, insurance, real estate, and transportation were most likely to have and support remote work (retail and education were least likely candidates). The trend is only increasing: the 2016 Gallup poll also found that those who work remotely log more hours away from the office than was reported in their 2012 findings. Not only are people logging more hours, but remote workers are saving money when it comes to commuting costs and businesses are saving on office space expenses.
Why is remote access important?
Software organizations where development engineers need to connect across multiple locations, small organizations lacking office-space, and large, enterprise organizations all want to offer the most flexible work options in order to attract high-ranking candidates and reap the rewards of having such a policy.
Who grants access to a business unit?
Access privileges are granted by the Data Custodians, Principal Administrator, or Managers of a Business unit or application owners responsible for the information being accessed.
Does Cambridge College have a VPN?
In the past, the College relied on a Virtual Private Network (VPN) to connect remote users directly to the College network. With overhead and support for this type of technology solution running in the multiple thousands per year the College has sought out alternative solutions for this basic service.
What is remote access policy?
A remote access policy can specify one or more of these attributes that should be checked before allowing access. If a policy specifies multiple conditions, then all of the conditions need to match in order for the policy to find a match. For example, let's say that a remote access policy will only allow VPN connections on Saturdays and Sundays, ...
What is the type of media used by the access client?
The type of media that is used by the access client, such as a plain old telephone line, ISDN, wireless, or VPN connection.
What is authentication type?
Authentication Type The type of authentication that is being used by the access client. Authentication types include CHAP, EAP, MS-CHAP, and MS-CHAP v2.
What is NAS authentication?
The vendor of the network access server (NAS) that is requesting authentication—this is most often used in a site-to-site VPN like the ones discussed in Chapter 7. You can use this attribute to configure separate policies for different NAS manufacturers who are connecting via IAS.
Do you need a separate remote access policy for each group?
The names of the groups to which the user or computer account that is attempting the connection belongs. You don't need to have a separate remote access policy for each group. Instead, you can use multiple groups or nested groups to consolidate and delegate the administration of group membership.