Remote secure access VPN provides remote and secure access to a company network to individual hosts or clients, such as telecommuters, mobile users, and extranet consumers. Each host typically has VPN client software loaded or uses a web-based client.
How to access home network remotely VPN?
to point you guys in the right direction:
- setup dynamic DNS for server & client
- setup an OpenVPN server
- setup an OpenVPN client
- open ports to/from server & client sides
How to speed up VPN remote access?
How to speed up a VPN
- Choose another server. Connecting to your nearest server will usually offer the best performance, but there are occasional exceptions.
- Refresh your system. If speeds are notably worse than unusual with several servers, the problem could be closer to home. ...
- Switch protocol. ...
- Tweak protocol settings. ...
- Use a wired connection. ...
- Try split tunneling. ...
Is VPN really secure?
It is important to note that a VPN will not secure your information once you start sharing it if that website or business is breached. For instance, a VPN will not keep your information from being shared if Facebook, or your bank, or your credit card company, is breached by hackers.
How to install secure VPN?
- To change the default setup language, click the current language in the top-right corner of the screen. ...
- Wait while setup installs AVG Secure VPN on your PC. ...
- Click the red (OFF) slider to connect to AVG Secure VPN servers.

How does a remote access VPN Work?
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
What is the difference between VPN and remote access?
A VPN is a smaller private network that runs on top of a larger public network, while Remote Desktop is a type of software that allows users to remotely control a computer. 2. Remote Desktop allows access and control to a specific computer, while VPN only allows access to shared network resources.
Do you need VPN for remote access?
No, but they serve a similar function. A VPN lets you access a secure network. RDP lets you remotely access a specific computer. Both will (usually) encrypt your traffic in one way or another, and both will grant you private access to a server or device that might be thousands of miles away.
What are the disadvantages of VPN?
VPN disadvantages#1: Not designed for continuous use. The use case for remote access VPN was never to connect an entire enterprise to the WAN. ... #2: Complexity impedes scalability. ... #3: Lack of granular security. ... #4: Unpredictable performance. ... #5: Unreliable availability.
Which VPN is best for remote access?
Perimeter 81 – Best all-round business VPN. Jul 2022. ... GoodAccess – Security Strategy Options. Apps Available: ... ExpressVPN – Lightning Fast VPN. ... Windscribe – VPN with Enterprise-Friendly Features. ... VyprVPN – Secure VPN with Business Packages. ... NordVPN – Security-first VPN. ... Surfshark – VPN with Unlimited User Connections.
How do I setup remote access to VPN?
Configure Remote Access as a VPN ServerOn the VPN server, in Server Manager, select the Notifications flag.In the Tasks menu, select Open the Getting Started Wizard. ... Select Deploy VPN only. ... Right-click the VPN server, then select Configure and Enable Routing and Remote Access.More items...•
Which is more secure VPN or remote desktop?
Security. Although both VPN and RDP are encrypted through internet connection, a VPN connection is less accessible to threats than a remote desktop connection. For this reason, VPN is often considered more secure than RDP.
Why you shouldn't use a VPN?
The 10 biggest VPN disadvantages are: A VPN won't give you complete anonymity: Read more. Your privacy isn't always guaranteed: Read more. Using a VPN is illegal in some countries: Read more. A safe, top-quality VPN will cost you money: Read more.
When should you not use a VPN?
When should you not use a VPN? One reason you may not use a VPN is when gaming or downloading, as a VPN can sometimes slow your connection speed. The other time to pause your VPN, is when you want to access content that is only available in your location.
When you're using a VPN who can still see your Internet traffic?
VPNs encrypt all internet traffic, effectively hiding your browsing history from your ISP. However, that doesn't mean the ISP is blind to your activities. They may be able to tell that you're connected to a VPN and for how long, based on the fact that the encrypted traffic is headed to an IP address of a VPN server.
Which is better VPN or remote desktop?
Security. Although both VPN and RDP are encrypted through internet connection, a VPN connection is less accessible to threats than a remote desktop connection. For this reason, VPN is often considered more secure than RDP.
Which is faster VPN or remote desktop?
The biggest advantage of RDP is that you have access to network resources, databases, and line-of-business software applications without the limitations and high bandwidth demands of VPN. Because so little data passes through the connection, RDP is ideal for low-bandwidth environments.
Is Chrome remote desktop a VPN?
Chrome Remote Desktop - A Better VPN and RDP Solution.
What is remote access VPN?
What is a remote access VPN? Businesses use remote access VPNs to establish a secure connection between their network and the devices used by remote workers. Once connected, employees are able to access the resources on the network just as if their devices were physically plugged in at the office.
What is site to site VPN?
A site-to-site VPN uses a secure gateway to connect a network at one location to one or more networks at another location. This type of VPN doesn’t require each device at the end location to have a VPN client installed because the gateway handles the traffic.
Is VPN a security initiative?
Top VPN brands join security initiative. Ethics and VPN: the industry needs to aim higher. While VPNs have grown increasingly popular among users looking to protect their data and privacy online, using the right type of VPN can make all the difference when working remotely.
Is remote access VPN secure?
Since remote access VPNs are affordable and secure, organizations can feel more comfortable with letting their employees work from home or while traveling.
What is remote access VPN?
A remote access Virtual Private Network (VPN) allows users working remotely to access and use applications and data residing in the corporate data center,headquarter offices, and cloud locations, often encrypting all user traffic.
How do remote access VPNs work?
Remote access VPNs create virtually 'private' tunnels between an organization's network and a remote user, regardless of the user's location.
Why are remote access VPNs becoming obsolete?
The days of network-centric security are over. For almost three decades, enterprises have relied on castle-and-moat methods to connect users to the network, and by extension, the applications running on it.
Why is a SASE approach better than remote access VPN?
SASE is a framework identified by Gartner as the way to securely connect entities such as users and devices to applications and services when their locations may be anywhere.
Why is zero trust network access (ZTNA) preferred over remote access VPN?
Zero trust network access (ZTNA) takes a user- and application-centric approach to private application access, ensuring that only authorized users have access to specific private applications by creating secure segments of one between individual devices and apps. That means no more network access, no more lateral movement.
What is Zscaler Private Access (ZPA)?
Zscaler Private Access (ZPA) is a cloud service from Zscaler that provides seamless, zero trust access to private applications running on the public cloud or within the data center. With ZPA, applications are never exposed to the internet, making them completely invisible to unauthorized users.
Why is ZPA superior to remote access VPN?
In contrast to VPN, ZPA is a more modern, robust security solution offering the following benefits:
What is remote access VPN?
For a relatively low price, a remote secure access VPN helps both small and medium-sized businesses give their remote workers secure and convenient access to the company’s private servers and reduce a possible exposure to cyberattacks.
What is VPN benefit?
VPN Benefits. Encryption of all transmitted data can be done within in a single session between the client and server using TLS. This is the widely used client to server standard used to secure web traffic to banks, hospitals, web search, etc. Another method is to create a Virtual Private Network ...
Why do businesses use VPN?
The end result is the same. Businesses use remote secure access VPN to make sure the connections between their networks, offices and remote devices are secure. The main advantage of remote secure access is the ability to provide individual users a way to remotely and securely connect to a computer network through an encrypted tunnel ...
What is secure remote access?
Secure remote access refers to any security policy, solution, strategy or process that exists to prevent unauthorized access to your network, its resources, or any confidential or sensitive data. Essentially, secure remote access is a mix of security strategies and not necessarily one specific technology like a VPN.
What technologies are used for secure remote access?
Secure remote access is comprised of a multitude of security solutions and technologies. Some of the most prominent include the following:
Secure remote access solution
Enables employees with precise access to the applications and data required to do their job from anywhere.
Why is secure remote access important?
With the work from home shift in the workforce, endpoints are accessing corporate networks from multiple locations. Today, employees’ home networks are often the originating point for network connections, multiplying the risk on both home and corporate networks.
What are the benefits of secure remote access?
While the benefits of secure remote access are numerous, there are four key advantages in which to focus on:
Can secure remote access be achieved without VPN?
Yes. A robust cloud-based, highly secure remote access solution can provide unified protection for virtually all users against web-based threats — independent of a VPN connection.
How can AT&T help organizations with secure remote access?
AT&T Cybersecurity is uniquely positioned to help organizations address these immediate challenges with an eye toward the future by helping them balance connectivity, collaboration, and cybersecurity affordably.
What are the advantages of VPN?
In summary, when comparing VPNs to other WAN technologies, VPNs have several advantages. For instance, consider a company with more than 500 small retail locations. The company could create a private WAN using leased lines, or Frame Relay, Ethernet WAN, Multiprotocol Label Switching (MPLS), and so on. However, each branch could instead have an ...
What is a header in a VPN?
headers including fields that allow the VPN devices to make the traffic secure. The VPN devices also encrypt the original IP packet, meaning that the original packet’s contents are indecipherable to anyone who happens to see a copy of the packet as it traverses the Internet.
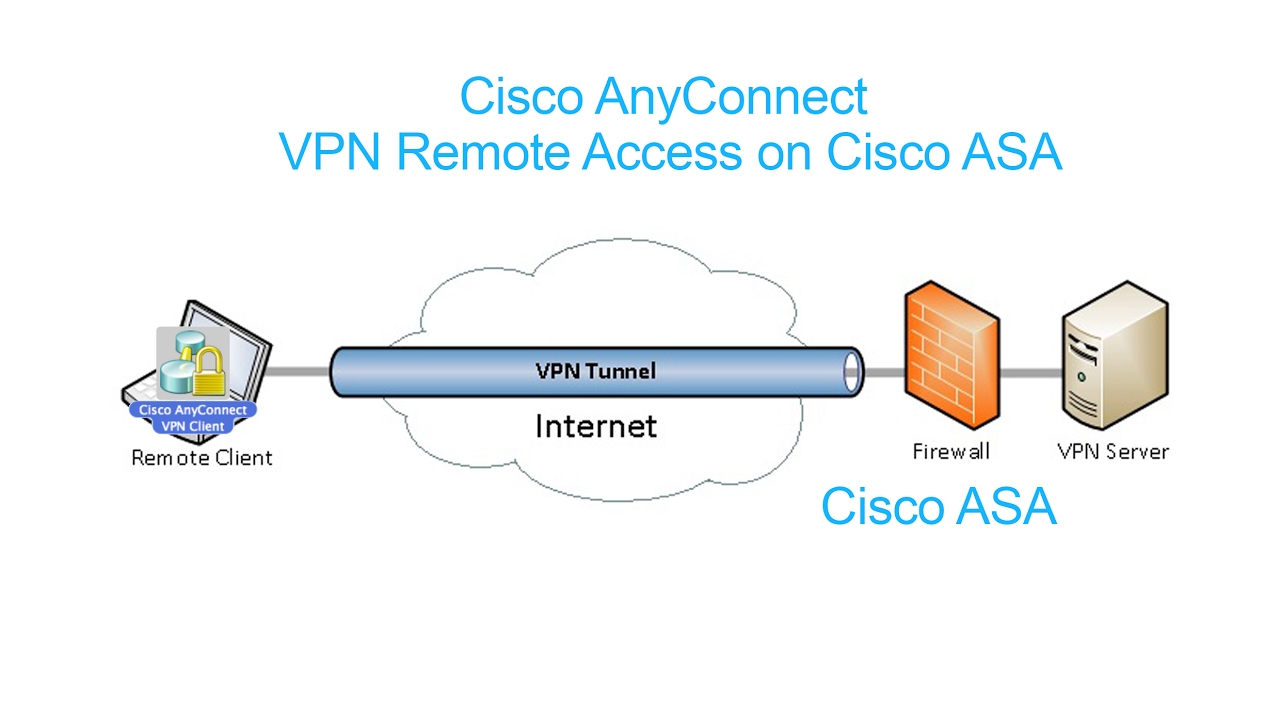
What is Cisco ASA?
Adaptive Security Appliances (ASA): The Cisco leading security appliance that can be configured for many security functions, including acting as a VPN concentrator, supporting large numbers of VPN tunnels. VPN client: For remote-access VPNs, the PC might need to do the VPN functions; the laptop needs software to do those functions, ...
Is VPN cheaper than WAN?
Cost: Internet VPN solutions can be cheaper than alternative private WAN options. Security: Internet VPN solutions can be as secure as private WAN connections. Scalability: Internet VPN solutions scale to many sites at a reasonable cost. Each site connects via any Internet.
Does a VPN gateway encrypt data?
Whenever the host tries to send any information, the VPN client software encapsulates and encrypts the information before sending it over the Internet to the VPN gateway at the edge of the target network. On receipt, the VPN gateway handles the data in the same way as it would handle data from a site-to-site VPN.
Why is VPN so bad?
Trust is inherent and often excessive for those inside the network. 2. There is a increased risk of external access to the network.
What is ZTNA security?
ZTNA takes a user-to-application approach rather than a network-centric approach to security . The network becomes deemphasized, and the internet becomes the new corporate network, leveraging end-to-end encrypted TLS micro-tunnels instead of MPLS.
Why are IPs never exposed to the internet?
IPs are never exposed to the internet, creating a “darknet” and making the network impossible to find. Apps segmentation ensures that once users are authorized, application access is granted on a one-to-one basis so that authorized users have access only to specific applications rather than full access to the network.
How does ZTNA improve security?
ZTNA improves your security posture by drastically reducing your attack surface. Application access is decoupled from network access. ZTNA moves away from network-centric security and instead focuses on securing the connection between user and application.
Does ZTNA require VPN?
Here’s how: ZTNA delivers a better experience for remote users. There’s no need to log into a cumbersome VPN. Instead, access is continuous regardless of changes to network connectivity. Moreover, ZTNA reduces access latency for faster experiences—regardless of location.
Can a VPN be found by adversaries?
Opening the network in this way enables it to be “found” by your remote users, but it also means it can be found by adversaries. They can (and do) exploit the VPN attack surface to infiltrate the network, deliver malware such as ransomware, launch denial-of-service attacks, and exfiltrate critical business data.
How does secure remote access work?
Enabling remote access means walking a tightrope between usability and cybersecurity. Every remote worker needs a way to connect with remote desktop services and applications that won't slow down their workflows. At the same time, IT administrators must manage those connections to ensure they don't leave the network open to threats.
Why is secure remote access important to remote work security?
Secure remote access approaches are so vital because it’s now impossible to control security at the endpoint. Each user in a remote or hybrid workforce is connecting to the network from a different type of computer or smartphone, and they’re using a variety of internet connections to log in.
What are the options for secure remote access?
Multiple solutions go into a comprehensive secure remote access package—and each one delivers vital functionality that reflects the way companies use their networks today. These features work together to protect users, data, and network assets in a distinct way.
Next-gen remote access solutions for a secure digital workspace
Learn how remote access solutions can secure digital workspaces and enhance the user experience.
Citrix solutions for secure remote access
Citrix secure access solutions take several forms to give companies a balanced selection of options based on their specific requirements. Whatever level of engagement with remote work these businesses have, there is a secure remote access solution for the situation.
What is a VPN service?
Synonymous with VPN service, this is a service you sign up for that allows you to connect to a virtual private network by providing a temporary IP address that hides your actual address.
Why do people use VPNs?
One of the main reasons users rely on VPNs? They want to get around geo-restrictions. These restrictions are often put in place by entertainment companies that only want to distribute content to certain regions. For instance, Netflix might offer content in the United States that it doesn't show in the UK. It might offer programming in the UK that Netflix users in the United States can't access. By using a VPN with an IP address based in the UK, U.S. viewers can try to access Netflix programming that isn't available in their home country. The VPN service — and the VPN connection — hides the location where the actual internet connection is made. Check your streaming service agreement for its Terms of Service, and also be mindful that some countries may have penalties for using VPN to circumvent its rules.
Why do we need VPN?
Your devices can be prime targets for cybercriminals when you access the internet, especially if you’re on a public Wi-Fi network.
How does VPN protect against identity theft?
A VPN can help protect against identity theft by helping protect your data.
What is VPN protocol?
VPN providers use these protocols to make sure that users are able to connect securely to a virtual private network. There are several VPN protocols available, all with their own strengths and weaknesses.
What happens if a VPN fails?
But what happens if a VPN provider’s network connection fails? Your computer or mobile device will default back to the public IP address provided by your ISP. This means that your online activity can now be tracked. A kill switch, though, prevents this from happening. If your VPN provider’s connection fails, the kill-switch feature severs your connection to the Internet completely. This way, your online activity won't be monitored by others. Not all VPN providers offer this feature, so look for it when shopping around.
Why is encryption important?
Encryption is essential to helping keep your data unreadable by hackers, private companies, and possibly by government agencies. Encryption jumbles up your data so that others can't make sense of it without the specific decryption key. AES, which stands for Advanced Encryption Standard, was an encryption method developed by Belgium cryptographers Joan Daemen and Vincent Rijmen. In 2002, AES became the U.S. federal standard for encryption. It has since become the standard form of encryption for the rest of the world, too.
