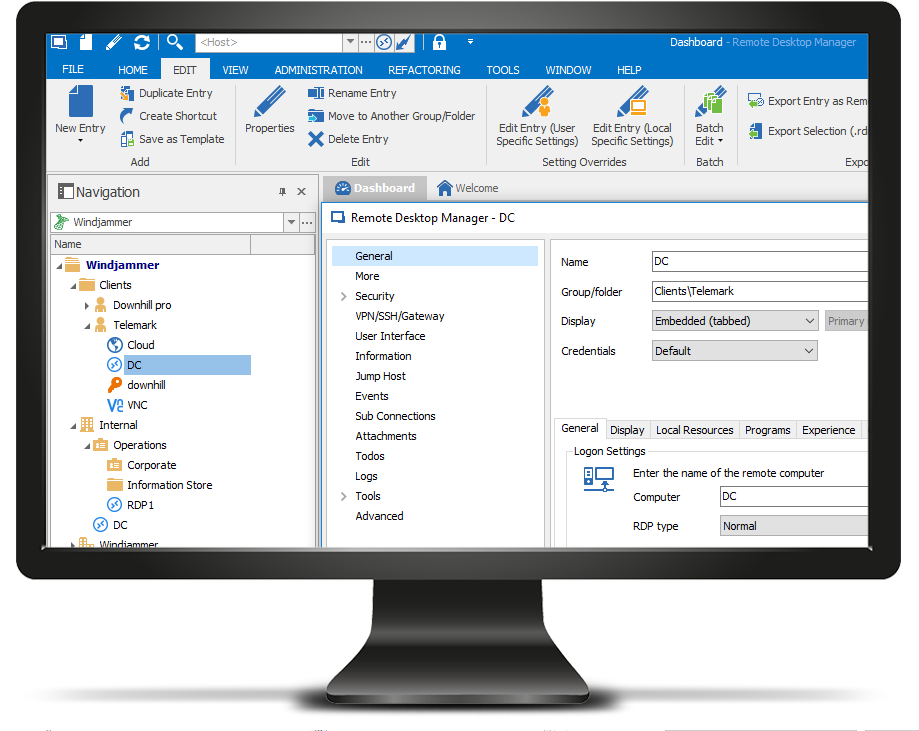
A Remote Access Connection Manager (RasMan) is a service provided by Windows that manages VPN
Virtual private network
A virtual private network extends a private network across a public network, and enables users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network. Applications running on a computing device, e.g. …
How to setup remote access?
Once installed, you can now connect to remote endpoints by following the steps below:
- The software needs to be downloaded on both the local and remote computers.
- Open the software on both the local and remote computers.
- Write down the ITarian ID number and password of the remote computer.
- Click “Start Connection.”
- Enter the ID number and password of the remote computer.
- Click “Connect.”
How do I enable remote access in Windows 10?
Windows 10 Fall Creator Update (1709) or later
- On the device you want to connect to, select Start and then click the Settings icon on the left.
- Select the System group followed by the Remote Desktop item.
- Use the slider to enable Remote Desktop.
- It is also recommended to keep the PC awake and discoverable to facilitate connections. ...
How secure is enabling remote access?
- iOS/Android: Swap album and artist titles in CarPlay/Android Auto.
- iOS/Android: Rare crash if your library had ~200,000 items.
- Desktop: Reduce hover play background size to allow clicking on poster.
- iOS: Crash for high CPU in some cases if server disks were offline.
- CarPlay/Android Auto: Show all albums when album types are enabled.
Can someone help me with remote access?
Windows Remote Assistance lets someone you trust take over your PC and fix a problem from wherever they are. Before you can use it, you'll need to enable access. In the search box on the taskbar, type remote assistance, and then select Allow Remote Assistance invitations to be sent from this computer from the list of results.
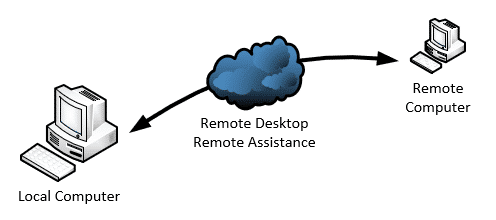
How to disable remote access?
You can disable it by clicking the "Start" button and then typing "services.msc" into the search bar. Press the "Enter" button and scroll down the list of Local Services to highlight the Remote Access Connection Manager. Right-click the service and select "Properties.". Click the drop-down menu next to "Startup Type" and select "Manual.".
How to disable remote access connection manager?
This file can sometimes take up a lot of system resources, so if you do not use a VPN or dial-up connection, you may want to disable it on the computer. You can disable it by clicking the "Start" button and then typing "services.msc" into the search bar. Press the "Enter" button and scroll down the list of Local Services to highlight the Remote Access Connection Manager. Right-click the service and select "Properties." Click the drop-down menu next to "Startup Type" and select "Manual." Click the "Stop" button under Service status and click "OK" to disable Remote Access Connection Manager.
How to change dial up settings for Remote Access Connection Manager?
You can change the dial-up settings for Remote Access Connection Manager by clicking the "Start" button, then clicking "Settings" and "Network & Internet.". Click the "Dial-up" connection option in Network & Internet and select the "Connect" button.
How to change remote access settings?
There is no control panel for Remote Access Connection Manager, but you can change the settings for it by changing your VPN or dial-up settings. Click the "Start" button and then select "Settings" followed by "Network & Internet," "VPN" and then "Advanced options.".
What is VPN connection?
About Virtual Private Networks. A virtual private network (VPN) connection is a secure network connection made from your computer to a private network. You may use a VPN connection to access your company's internal server so that you can work from home, for example.
What is Citrix Networking?
With Citrix Networking and SmartAccess, organizations have the capability to control printers, client devices, session connectivity, and reactive security postures. Admins are also able to leverage the full capabilities of Citrix Analytics to collect data for improving app performance, supporting continuous operations, and enhancing security.
What happens when an employee is displaced due to a business continuity disruption?
If an employee has been displaced due to a business continuity disruption, they can continue to be productive using a secure remote access connection.
Why is remote access important?
It is valuable for businesses to have a strategy for allowing remote access to their users.
Why is it important to have a bring your own device?
With remote access, data stays secure and workers can be productive at any location. By allowing employees to use their own device, businesses can exponentially lower the costs of purchasing and managing corporate-owned devices.
What is remote access?
Remote access is the act of connecting to IT services, applications or data from a location other than headquarters or a location closest to the data center. This connection allows users to access a network or computer remotely via an internet connection or telecommunications. Secure remote access benefits include: ...
What is remote access?
Remote access is the ability for an authorized person to access a computer or network from a geographical distance through a network connection.
How does remote access work?
Remote access is accomplished with a combination of software, hardware and network connectivity.
What are the types of remote access?
Traditionally, enterprises used modems and dial-up technologies to allow employees to connect to office networks via telephone networks connected to remote access servers. Devices connected to dial-up networks use analog modems to call assigned telephone numbers to make connections and send or receive messages.
What is remote access?
Remote Access is simply reaching a remote machine, most often a computer, to carry out a particular task. In most cases, Remote Access is used to troubleshoot a target computer that is situated geographically at a different place.
What percentage of the workforce will be remote workers by 2027?
By the year 2027, almost 50 percent of the US workforce is expected to be working remotely. With this many making the switch to remote work, it is essential to have a proper remote access solution in place to maintain business continuity. Here are some of the reasons why every enterprise needs remote access software.
Is Remote Access Plus secure?
This is why Remote Access Plus comes with data privacy and security as its core mantra, which is reflected in features like recording remote sessions, prompting user confirmation for each session, and idle session timeout.
Does remote access require hardware?
It does not require any additional hardware to do so. Instead, it requires remote access software to be downloaded and installed on both the local and remote computers. Once the software is installed, the local computer can access the remote computer and perform several tasks like running applications, managing updates, ...
Why should remote desktop services have centralized RDS?
Because the remote desktop service should have the centralized RDS and hence the ability of RDS should be powerful enough to withstand the functional load of the several computer systems. The network should be reliable and adjusted to fit into the properly aligned network.
How does VPN work?
It is used to communicate all the hosts by a wired interface network or via internet connection or means of Wi-Fi network interface. The VPN is used to link every individual network to the allotted private networks. By using remote access, the VPN has the capability of connecting every private network to the VPN server.
What is a direct remote access line?
It is the direct remote access which is integrated as the direct line from the organization’s LAN to the employee laptop or desktop. The same line is also used to link both the home and the company’s LAN. The direct connection offers robust speed, but the maintenance and cost are expensive. The LAN cable leads to an improper connection, which is prone to data loss and loose connection that affects productivity. So the damage causes the failure of cables because of the external conditions such as construction work and weather conditions.
What is VPN in business?
VPN. The other method which is established on the internet to link to the remote sites by using a virtual private network. It uses tunnel methods and encryption to manage and access the network of the company. It is perfectly ideal for small-scale industries.
Why is my LAN cable failing?
The LAN cable leads to an improper connection, which is prone to data loss and loose connection that affects productivity. So the damage causes the failure of cables because of the external conditions such as construction work and weather conditions. 2. VPN.
Why is disaster recovery important?
Advantages: Disaster recovery is easily performed to retrieve the lost documents and files which are stored in a secured data center. So in remote desktop connection, there is no need for anxiety to theft or data. The connections to check the correspondence should be secured and safe to prevent hacking.
What is remote access control?
The remote access is a method to establish a connection over the server, and it extends the ability to access the network. It allows the user to manage and view the system to fix any faults or requirements when it is not able to connect physically. In other terms, the user can access the system with an internet connection or telecommunication method. IT employees and company chief who are traveling to a different location should need to access the computer networks by using remote access control.
What is remote management?
Definition of Remote Management. Remote Management is managing a computer or a network from a remote location. It involves installing software and managing all activities on the systems/network, workstations, servers or endpoints of a client, from a remote location.
What is remote monitoring?
Remote Monitoring (also shortened to RMON) refers to the specification that helps MSPs monitor network operational activities of their clients by using remote devices, which are known as probes or monitors. This helps MSPs ensure efficient network infrastructure control and management.
What does RMM stand for?
The acronym RMM stands for Remote Monitoring and Management. Thus there are two aspects involved- the remote monitoring aspect and the remote management aspect, both of which must be discussed separately.
What is PSA RMM?
What's PSA RMM? PSA (professional services automation) tools play a key role in the workings of any MSP. PSA tools help track customer information, work done, and more. They also generate invoices from the work.
What should a remote access policy cover?
To be effective, a remote access policy should cover everything related to network access for remote workers. Organizations must identify which users should be given access, since not everyone may benefit from having the privilege. For example, it might not be a good idea to give remote access to users with access to sensitive data ...
What are the considerations when formulating a remote access policy?
Other considerations when formulating a remote access policy include but are not limited to the following: Standardized hardware and software, including firewalls and antivirus/antimalware programs. Data and network encryption standards. Information security and confidentiality. Email usage.
What is remote work?
Remote work has brought with it a few challenges, including potential computer and network security risks. There is a real need for guidelines surrounding remote access, along with other policies. A remote access policy serves as a guide for remote users connecting to the network. It extends the policies governing network and computer use in ...
Can you customize remote access policy?
Always ensure that your remote access policy is not an exact copy of another organization’s template; rather, you should customize it depending on your requirements. Otherwise, it might not be that useful for your organization.
Workforce Access Management vs Customer Access Management
Software vendors and solution providers offer two different types of access management solutions. Workforce access management solutions are used to authenticate and authorize employees and contractors accessing corporate applications and IT systems.
Multi-Factor Authentication
Most access management solutions support Multi-Factor Authentication (MFA) functionality to protect against user impersonation and credential theft. With MFA, a user must present multiple forms of evidence to gain access to an application or system, for example, a password and a one-time, short-lived SMS code.
Single Sign-On
Most access management solutions support Single Sign-On (SSO) capabilities to allow users to access all their applications and services using a single set of credentials. SSO improves user experiences by eliminating password sprawl and frustration.
