What is secure remote access protocol?
PPTP is a remote access protocol, based on PPP, created by Microsoft. It's used to establish virtual connections across the internet via PPP and TCP/IP, enabling two networks to use the internet as their WAN link while retaining the security benefits of a private network.
Which method of remote access is the most secure?
Implement a Secure Connection for Remote Network AccessWired Connection: A wired connection is the most secure method for remote network access.Home Wi-Fi: The second most secure network connection is using a secured home Wi-Fi connection.More items...•
Which of the following protocols are used for secure remote access services?
One of these protocols is Remote Desktop Protocol or RDP. Remote Desktop Protocol or RDP is a communications protocol designed to manage remote access to desktops, files, systems, and even private networks.
Who is more secure protocol for remote login?
While Remote Desktop is more secure than remote administration tools such as VNC that do not encrypt the entire session, any time Administrator access to a system is granted remotely there are risks. The following tips will help to secure Remote Desktop access to both desktops and servers that you support.
What are the types of remote access?
Remote Access Control MethodsDirect (Physical) Line. The first direct remote access control that can be implemented is a direct line from a computer to the company's LAN. ... Virtual Private Network. Another method which is more common is establishing a VPN. ... Deploying Microsoft RDS.
Why is secure remote access important?
A secure remote access system protects your employees from web-based threats such as phishing attacks, ransomware and malware while they're logged in to your company's network. These cyber incidents can lead to unauthorized access and use of both the company's business data and the employee's personal data.
What is secure remote access VPN?
A remote access virtual private network (VPN) enables users who are working remotely to securely access and use applications and data that reside in the corporate data center and headquarters, encrypting all traffic the users send and receive.
Which of the following protocol is used by remote login?
Notes: Telnet is a protocol used to log in to remote computers. terminals over the Internet or a TCP/IP computer network.
Which of the following protocols provide access to a remote host?
DNS is important because it can quickly provide users with information, as well as access to remote hosts and resources across the internet. Dynamic Host Configuration Protocol.
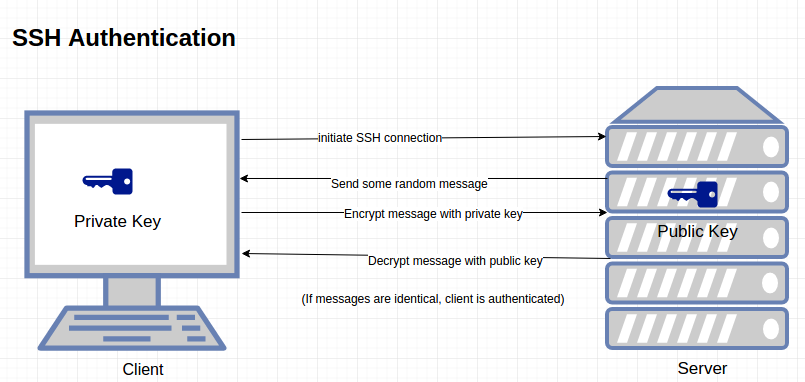
Is SSH secure?
SSH provides password or public-key based authentication and encrypts connections between two network endpoints. It is a secure alternative to legacy login protocols (such as telnet, rlogin) and insecure file transfer methods (such as FTP).
Is SSH A protocol?
SSH or Secure Shell is a network communication protocol that enables two computers to communicate (c.f http or hypertext transfer protocol, which is the protocol used to transfer hypertext such as web pages) and share data.
Is Telnet a secure protocol?
Telnet is inherently insecure. Credential information (usernames and passwords) submitted through telnet is not encrypted and is therefore vulnerable to identity theft. However, users can establish an Secure Shell connection instead to prevent this type of intrusion.
What is the technology used in remote access?
virtual private network (VPN) technologyRemote access software is usually accomplished using a virtual private network (VPN) technology. This type of method is more available compared to others since it is a more secure remote access software that connects the user and the enterprise's networks through an internet connection.
What are the characteristics of various remote access security technologies?
Highly secure mobile computing - even in IPsec-hostile remote access environments. VPN tunnel without interrupting mobile computing sessions. Optimized network access control for remote access environments. Optimized network access control for remote access environments.
How do I access network resources?
Press Windows Logo+R (or select Start, All Programs, Accessories, Run) to open the Run dialog box. Type the network address for a shared resource, and then click OK to open the resource in a folder window. In a program's Open or Save As dialog box, you can type a network address in the File Name text box.
What is Microsoft protocol that allows a user to view and control the desktop of a remote computer?
Microsoft Remote Desktop Protocol (RDP)The Microsoft Remote Desktop Protocol (RDP) provides remote display and input capabilities over network connections for Windows-based applications running on a server. RDP is designed to support different types of network topologies and multiple LAN protocols.
What is secure remote access?
Secure remote access refers to any security policy, solution, strategy or process that exists to prevent unauthorized access to your network, its resources, or any confidential or sensitive data. Essentially, secure remote access is a mix of security strategies and not necessarily one specific technology like a VPN.
What technologies are used for secure remote access?
Secure remote access is comprised of a multitude of security solutions and technologies. Some of the most prominent include the following:
Secure remote access solution
Enables employees with precise access to the applications and data required to do their job from anywhere.
Why is secure remote access important?
With the work from home shift in the workforce, endpoints are accessing corporate networks from multiple locations. Today, employees’ home networks are often the originating point for network connections, multiplying the risk on both home and corporate networks.
What are the benefits of secure remote access?
While the benefits of secure remote access are numerous, there are four key advantages in which to focus on:
Can secure remote access be achieved without VPN?
Yes. A robust cloud-based, highly secure remote access solution can provide unified protection for virtually all users against web-based threats — independent of a VPN connection.
How can AT&T help organizations with secure remote access?
AT&T Cybersecurity is uniquely positioned to help organizations address these immediate challenges with an eye toward the future by helping them balance connectivity, collaboration, and cybersecurity affordably.
What is remote access protocol?
A remote access protocol is responsible for managing the connection between a remote access server and a remote computer. It’s necessary for desktop sharing and remote access for help desk activities. The primary remote access protocols in use today are the Serial Line Internet Protocol (SLIP), Point-to-Point Protocol (PPP), ...
What is PPP protocol?
PPP is a remote access protocol that allows you to implement TCP/IP. It establishes a connection via point-to-point links (i.e., dedicated leased lines and dial-up). PPP is used most often for remote connections to LANs and ISPs. PPP utilizes the Link Control Protocol (LCP), which tests the link between client and PPP host ...
How to use PPTP?
To use PPTP, you’ll have to set up a PPP session between the server and the client, usually over the internet. Once the session is established, you’ll create a second dial-up session. This dial-up session will use PPTP to dial through the existing PPP session.
What is PPTP in a network?
PPTP is a remote access protocol, based on PPP, created by Microsoft. It’s used to establish virtual connections across the internet via PPP and TCP/IP, enabling two networks to use the internet as their WAN link while retaining the security benefits of a private network.
What is RDP in Citrix?
Finally, there is the RDP, which is very similar to the Independent Computing Architecture (ICA) protocol used by Citrix products. RDP is utilized to access Windows Terminal Services, which is a close relative of the product line provided by Citrix WinFrame.
What is managed services provider?
As a managed services provider (MSP), you likely already work with remote access protocols on a daily basis. But learning how to best explain the various types of remote access protocols and their advantages and disadvantages to customers is critical in helping them understand your decisions—and why they should trust you and your services.
Is RDP the same as ICA?
RDP offers the same core functions as ICA, although there are some limitations. RDP provides remote access for Windows clients only, while ICA can provide access for numerous platforms. ICA also offers support for automatic client updates, publishing an app to a web browser, and more.
What is RDP vulnerability?
RDP vulnerabilities are a popular, common exploit among cybercriminals for a number of different reasons. Some of the most common objectives of an RDP attack are distributed denial of service (DDoS) attacks and ransomware delivery.
What is DDoS amplification?
DDoS attackers use a variety of different methods for accomplishing this, such as large botnets or a technique called DDoS amplification, which takes advantage of a service that sends a much larger response than the initial request. DDoS attackers will send traffic to these services while masquerading as their target.
What is the most common delivery mechanism for ransomware in 2020?
The growing use of RDP during the COVID-19 pandemic made it the most common delivery mechanism for ransomware in 2020. After using RDP to gain access to an organization’s network, ransomware operators are then able to explore the network and plant ransomware on high-value systems.
Is RDP secure?
Most of the problems with setting up Remote Desktop Protocol (RDP) for remote work involves making RDP accessible via the public internet. RDP itself is not a secure setup and therefore requires additional security measures to keep workstations and servers protected. Without proper security protocols in place, organizations face several potential ...
Do VPNs have vulnerabilities?
However, while VPNs are a commonly used solution and a defense-in-depth security measure, they have vulnerabilities and are often targeted by cyber threat actors attempting to deploy malware. VPN users must recognize their inherent weaknesses and upload security patch upgrades when provided.
Is RDP a security risk?
Options for Securing RDP. RDP is a significant risk to an organization’s security. Several different options exist for securing RDP, which differ significantly in terms of effectiveness and usability.
Can an attacker gain full access to an organization's network?
With this initial compromise, the attacker will likely be able to gain full access to an organization’s exposed network. This can occur because these types of accounts are managed at the domain level by a centralized system, meaning that the same credentials are used for all systems.

Serial Line Internet Protocol (Slip)`
Point-To-Point Protocol
- PPP is a remote access protocol that allows you to implement TCP/IP. It establishes a connection via point-to-point links (i.e., dedicated leased lines and dial-up). PPP is used most often for remote connections to LANs and ISPs. PPP utilizes the Link Control Protocol (LCP), which tests the link between client and PPP host and specifies PPP client configuration, to communicate between h…
Point-To-Point Tunneling Protocol
- PPTP is a remote access protocol, based on PPP, created by Microsoft. It’s used to establish virtual connections across the internet via PPP and TCP/IP, enabling two networks to use the internet as their WAN link while retaining the security benefits of a private network. PPTP is a great option because it’s simple and secure. To use PPTP, you’ll ha...
Windows Remote Access Services
- Windows 2000 and Windows NT let users dial up a server and connect to both the server and the server’s host network. This is referred to as RAS, which is used in smaller networks where a dedicated dial-up router would not be possible or practical. With a RAS setup, you can connect a modem to a Windows 2000 or Windows NT server and configure the modem as dial-out only, di…
Remote Desktop Protocol
- Finally, there is the RDP, which is very similar to the Independent Computing Architecture (ICA) protocol used by Citrix products. RDP is utilized to access Windows Terminal Services, which is a close relative of the product line provided by Citrix WinFrame. RDP offers the same core functions as ICA, although there are some limitations. RDP provides remote access for Windows clients o…