Zero Trust Network Access (ZTNA) solutions, sometimes also referred to as SDP (software defined perimeter) solutions, are a VPN replacement representing a new conceptual approach to providing secure remote access.
How to get started with zero trust security?
The different areas are:
- Secure identity with Zero Trust
- Secure endpoints with Zero Trust
- Secure applications with Zero Trust
- Secure data with Zero Trust
- Secure infrastructure with Zero Trust
- Secure networks with Zero Trust
- Visibility, automation, and orchestration with Zero Trust
What is zero trust mean?
“Zero trust means you have to get into a system that locks you out until you prove otherwise,” he says, referring to proof that the persons seeking access are who they say they are and can prove it.
What is a zero trust security strategy?
What is a Zero Trust Architecture
- A Zero Trust Architecture. In Zero Trust, you identify a “protect surface.” The protect surface is made up of the network’s most critical and valuable data, assets, applications and services ...
- Zero Trust: As Dynamic as Your Enterprise. Zero Trust is not dependent on a location. ...
- Deploying Zero Trust. ...
What is a zero trust security solution?
Zero trust security solutions may grant or deny access based on criteria such as:
- User identity
- Geographic location
- Time of day
- Operating system and firmware version
- Device posture
- Endpoint hardware type
Is zscaler a zero trust?
Zscaler is the only cybersecurity vendor that offers a zero trust platform born in the cloud and designed for cloud organizations.
Is VPN or zero trust best for remote working security?
While VPNs do offer a level of connectivity, zero trust is specifically designed to meet modern needs for visibility and control as well as critical business demands such as remote work, speed, performance, security and more.
What technologies does zero trust require?
Zero Trust also requires consideration of encryption of data, securing email, and verifying the hygiene of assets and endpoints before they connect to applications. Zero Trust is a significant departure from traditional network security which followed the “trust but verify” method.
Is zero trust widely accepted?
The Zero-Trust model has been widely recognized as an effective approach to prevent data breaches and mitigate the risk of supply chain attacks.
Will zero trust replace VPN?
VPNs don't address network security as deeply as zero trust network access (ZTNA), relying mostly on broad network-based protection. This means zero trust can be an excellent and more secure replacement for a VPN.
How does a zero trust network work?
Rooted in the principle of “never trust, always verify,” Zero Trust is designed to protect modern environments and enable digital transformation by using strong authentication methods, leveraging network segmentation, preventing lateral movement, providing Layer 7 threat prevention, and simplifying granular, “least ...
Which are the three components of zero trust?
There are three key components in a zero trust network: user/application authentication, device authentication, and trust.
What are the 3 stages of the Zero Trust security model?
assessment, control, and recovery operations. A Zero Trust solution requires operational capabilities that: Never trust, always verify – Treat every user, device, application/workload, and data flow as untrusted.
How do you implement zero trust in Microsoft?
Guiding principles of Zero TrustVerify explicitly - Always authenticate and authorize based on all available data points.Use least privilege access - Limit user access with Just-In-Time and Just-Enough-Access (JIT/JEA), risk-based adaptive policies, and data protection.More items...•
What are the disadvantages of zero trust?
The core challenge of zero trust is locking down access without bringing workflows to a grinding halt. People require access to sensitive data to work, communicate and collaborate. If individuals change roles and find themselves locked out of files or applications for a week, their productivity can plummet.
Is zero trust a fad?
Fact: Many Organizations Are Already Planning a Zero-Trust Approach to Security. Zero trust is no fad. It's a fundamental shift in the way that organizations approach network security, and it's becoming more common.
Why are companies moving to zero trust network model?
In the current threat environment, the federal government can no longer depend on conventional perimeter-based defenses to protect critical systems and data, according to the memorandum. A transition to a zero trust approach to security provides a defensible architecture for this new environment.
What is zero trust a model for more effective security?
Zero Trust is a security concept centered on the belief that organizations should not automatically trust anything inside or outside its perimeters and instead must verify anything and everything trying to connect to its systems before granting access. “The strategy around Zero Trust boils down to don't trust anyone.
Who created zero trust?
John KindervagIn 2010, John Kindervag, an analyst at Forrester Research, coined the term "zero trust," which centered around the idea that an organization shouldn't trust anything inside or outside its perimeters.
How does zero trust work?
The Zero Trust security framework helps organizations effectively meet these challenges by gating access to resources individually using granular access policies that take advantage of dynamic user and device risk signals and other telemetry to make more adaptive access decisions.
What is Microsoft Zero Trust Assessment?
We’ve created the Microsoft Zero Trust Assessment tool to help you determine where you are in your Zero Trust journey. Our assessment tool will help you assess your readiness across identities, devices, apps, infrastructure, network and data, and then provide go-dos and deployment guidance to help you reach key milestones.
Is Microsoft a leader in cybersecurity?
Microsoft is a leader in cybersecurity , and we embrace our responsibility to make the world a safer place.
What is Zero Trust?
Zero Trust (ZT) is an approach to network security and access control that meets the challenges of 21st Century cybersecurity. Also called Zero Trust Network Access (ZTNA) this new framework is based on one fundamental assumption:
What are the guiding principles behind Zero Trust?
In the machine-to-machine context, trust is an algorithmically-generated evaluation of an incoming connection. Based on many factors, the value of that evaluation will fall somewhere between complete trust (+1) and complete distrust (-1). “Zero” trust is simply the case when the system knows nothing about the incoming connection.
What are the benefits of Zero Trust?
Combining least privilege access, verify explicitly, and assume breach in a Zero Trust framework addresses the security weaknesses of legacy technologies. But the benefits of Zero Trust go much further.
What are the key questions to ask when considering a Zero Trust provider?
Choosing the wrong approach to Zero Trust leads to wasted money on projects that are ultimately abandoned. Asking the right questions about potential Zero Trust providers can make the difference between success and failure.
Why have companies been slow to adopt the Zero Trust model?
Google broke new ground by being the first Zero Trust implementation by a major enterprise. Unfortunately, the BeyondCorp initiative also set expectations that Zero Trust implementations are complicated, time-consuming, and expensive.
What is zero trust?
Instead of assuming everything behind the corporate firewall is safe, the Zero Trust model assumes breach and verifies each request as though it originates from an open network. Regardless of where the request originates or what resource it accesses, Zero Trust teaches us to “never trust, always verify.”.
What can help bring zero trust to life?
Solution providers and independent software vendors can help bring Zero Trust to life.
What is telemetry used for?
Use telemetry to detect attacks and anomalies, automatically block and flag risky behavior, and employ least privilege access principles.
What data points are used to authenticate and authorize?
Always authenticate and authorize based on all available data points, including user identity, location, device health, service or workload, data classification, and anomalies.
Who is the host of Zero Trust Essentials?
Learn about Zero Trust, the six areas of defense, and how Microsoft products can help in the first episode of Microsoft Mechanics’ Zero Trust Essentials series with host Jeremy Chapman.
Zero Trust Security Solutions Software Overview
Zero Trust Security Solutions offer a comprehensive set of features that provide secure access to IT resources. It protects users, applications, and data from unauthorized access and malicious actors.
Best Zero Trust Security Solutions Software include
Zscaler Internet Access, Zscaler Private Access, GoodAccess, Twingate, SecureLink Enterprise Access, Cloudflare Access, Appgate SDP, Google BeyondCorp, Wandera, and Proofpoint Meta (formerly Meta Networks).
Zero Trust Security Solutions Products
The list of products below is based purely on reviews (sorted from most to least). There is no paid placement and analyst opinions do not influence their rankings. Here is our Promise to Buyers to ensure information on our site is reliable, useful, and worthy of your trust.
What are Zero Trust Security Solutions?
Zero Trust Security Solutions offer a comprehensive set of features that provide secure access to IT resources. It protects users, applications, and data from unauthorized access and malicious actors.
Zero Trust Security Solutions Features
Zero trust security solutions will include many of the following features.
Zero Trust Security Solutions Comparison
When considering zero trust security solutions consider the following.
Pricing Information
Pricing of zero trust security solutions depends on the features provided, the scale of your operations, and the nature of your tech stack. As zero trust security solutions offer a range of options, and IT infrastructures vary greatly, obtaining a price quote from the vendor is the best approach to understanding its potential costs.
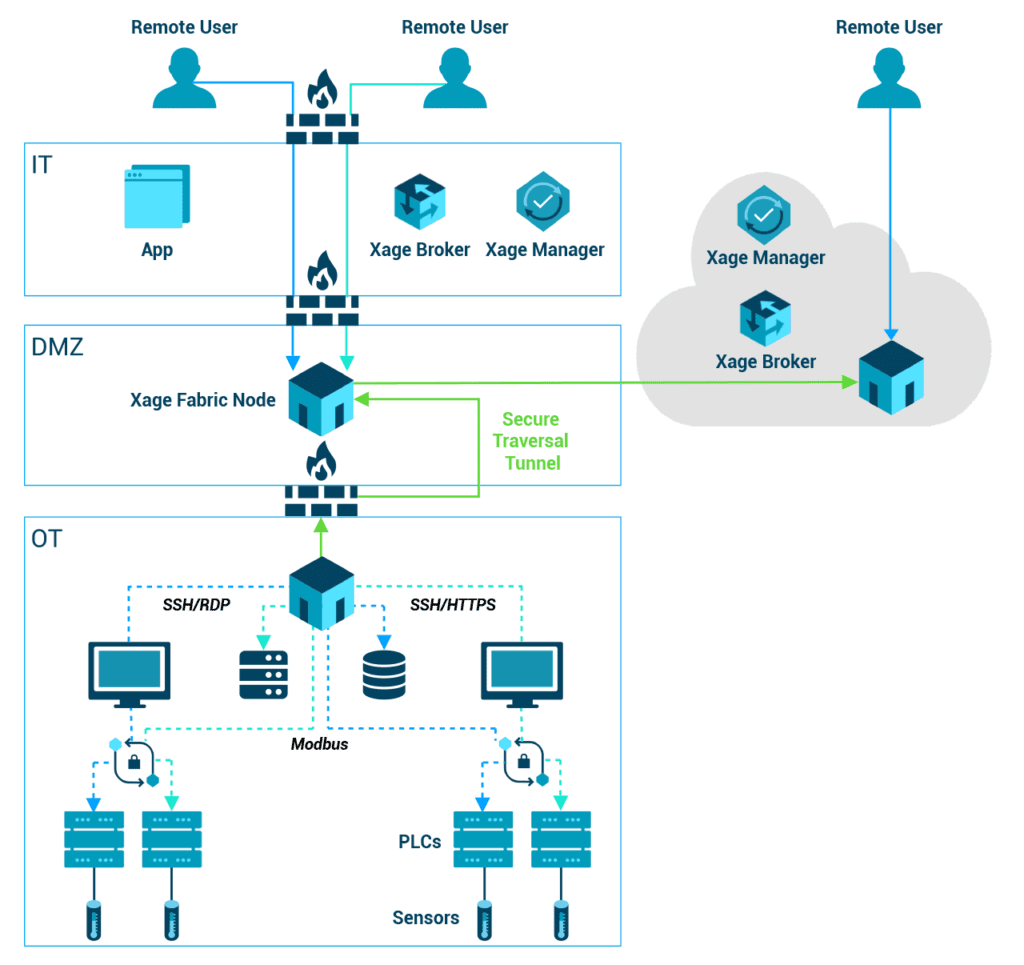
Common Remote Access Technologies Run Counter to Zero Trust
The urgency to “go remote” in response to the COVID-19 pandemic compelled organizations to lean into VPNs and remote access technologies, like remote desktop protocol (RDP), more heavily than ever. This seismic workplace shift magnified the considerable, pre-existing security faults inherent to many remote access technologies.
How to Align Remote Access with Zero Trust
A zero trust architecture (ZTA) treats all access requests as potentially malicious—a stark departure from the all-or-nothing access allowed by VPNs.
VPN Basics
VPNs were first introduced in 1995, when a consortium of companies led by Microsoft released Point-to-Point Tunneling Protocol (PPTP), a protocol that allowed the creation of a secure network between users by establishing a tunnel over a Local Area Network (LAN) or Wide Area Network (WAN) to enable movement of encrypted data through the tunnel.
The Downsides of VPNs
Corporate VPNs weren’t designed for today’s environment, which features many remote workers and extensive use of SaaS apps and cloud services. In fact, even before the pandemic-spurred mass move to work-from-home, VPNs were no longer able to serve the diverse secure remote access needs of today’s businesses and users.
The Zero Trust Model
The continuing onslaught of cyberattacks in recent years has overwhelmed conventional approaches to network security based on legacy technologies such as VPNs.
Zero Trust Network Access (ZTNA)
Zero Trust Network Access (ZTNA) solutions, sometimes also referred to as SDP (software defined perimeter) solutions, represent a new conceptual approach to providing secure remote access.
Implementing ZTNA
ZTNA solutions are an essential element of a comprehensive Zero Trust solution. While security experts recommend migrating to a comprehensive Zero Trust solution, rather than implementing Zero Trust on a piecemeal basis, for organizations that prefer a more gradual approach, ZTNA is an ideal place to start.
About Leo Versola
For over 25 years, Leo has executed on strategic business vision and technical leadership with a wide range of start-ups and established cybersecurity companies in various senior leadership roles.